SOLUTION
Application Security Risk Management
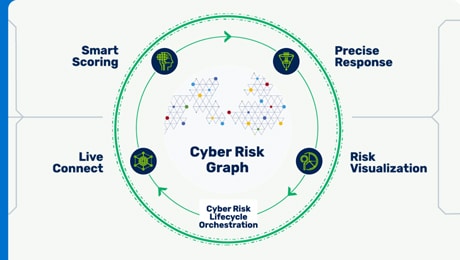
Aggregate application security tool findings to prioritize and reduce cyber risk across the entire software development lifecycle

Gain a complete understanding of your software assets
Visualize and understand your application attack surface with a centralized app inventory that incorporates application security tool findings, business context, and threat intelligence.
This single source of truth gives app owners a holistic view of the cyber risk associated with their applications. It also provides developers with one place to see all the security findings related to their code.
Prioritize the AppSec findings that matter
Use context that reflects relationships between apps, infrastructure, business priorities, and likelihood of exploit to determine risk and prioritize security findings.
Risk-based prioritization fosters trust among security, business and development teams by focusing everyone on fixing what matters to the business.
Brinqa automates the prioritization of application security findings from across all your application security tools.

Ship secure code efficiently
Evaluate cyber risk throughout the CI/CD pipeline to fix the application security findings that matter without slowing down developers.
Orchestrated workflows enhance ticketing in issue-tracking tools, automate ownership assignments, and enforce SLAs.
Brinqa provides enterprise application security risk management so you can prioritize and remediate the application security findings that matter to your business.

Monitor and communicate security posture to all stakeholders
Transform application security reporting from tool-centric to app-centric via cyber-hygiene dashboards, reports, and security scorecards.
Easily communicate application risk across your business in a language that motivates app owners and developers and streamlines action.
Brinqa combines application security and risk management in a single platform that both security and development teams will love.

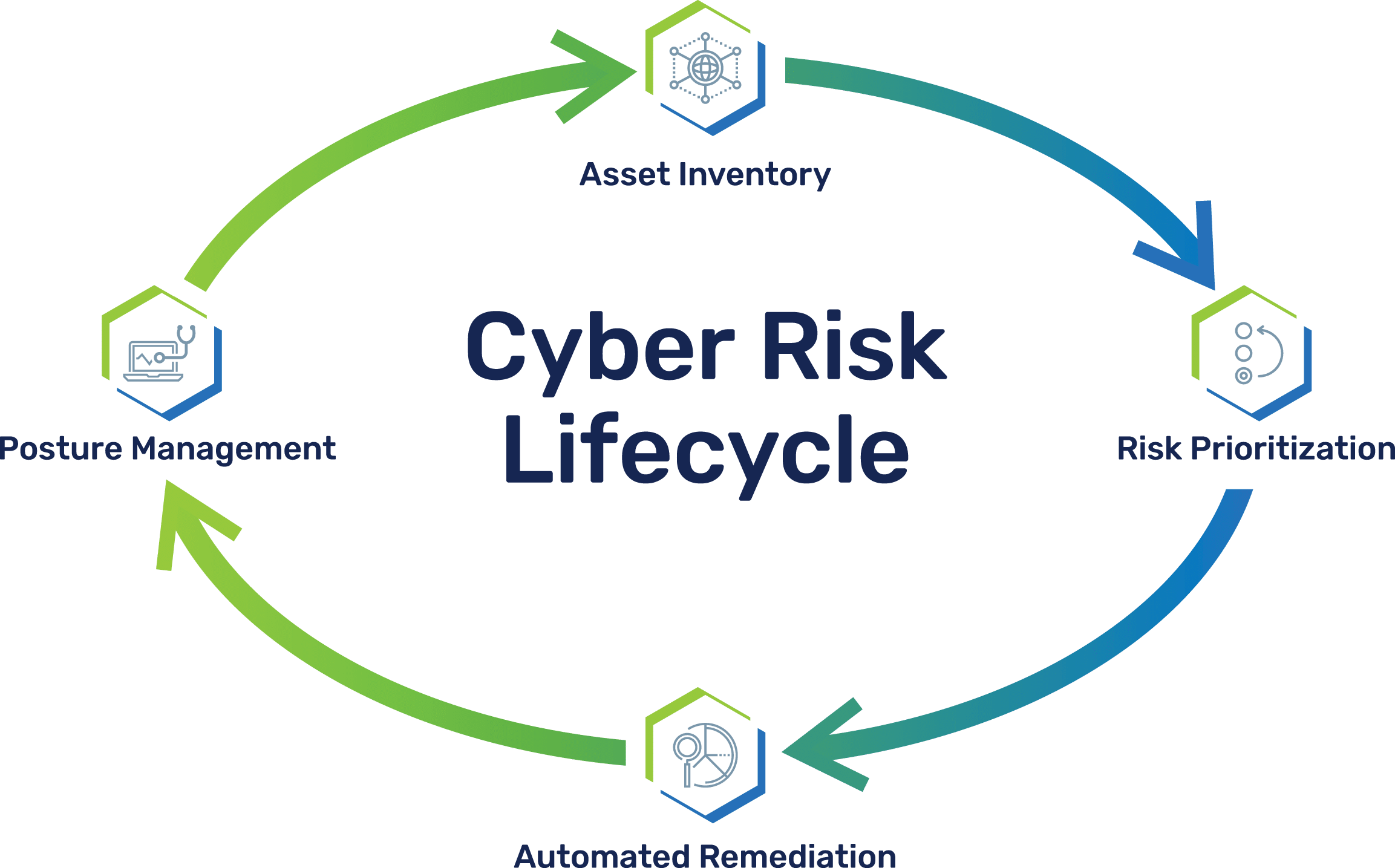
Conquer AppSec chaos
Brinqa provides one integrated platform to automate the cyber risk lifecycle across every stage of your SDLC so you can deliver secure code, faster
Experience the true power of the Brinqa platform in a demo.
Request Demo
FAQ
What is application security risk management?
Application security risk management aggregates and analyzes findings from security tools across software development, deployment and operations to improve visibility, prioritize vulnerabilities, enforce controls, and orchestrate remediation. Security leaders can use application security risk management to improve application security efficacy and better manage risk.
How to apply enterprise application risk prioritization?
Application security tools report an overwhelming number of findings. Prioritizing which of these findings and vulnerabilities pose true risk to the business is key to effective risk reduction.
Applying effective enterprise application risk prioritization requires a full understanding of assets, application dependencies and relationships, business context, and compensating controls.
What are the key components of application security risk management?
Application security risk management solutions must provide the following key capabilities:
- Collection and aggregation of findings from across the applications security stack (SAST, DAST, IAST, SCA, etc.)
- Correlation of security findings with business context, threat intelligence, and asset information to create a cyber risk graph that represents a complete risk-based understanding of the application environment
- Automatic prioritization of findings based on risk factors of the business, vulnerabilities, exploitability, and compensating controls
- Integration with ticketing and development tools to streamline remediation
- Reporting that provides business, security and application teams with the information they need to understand the risk to the business, who is responsible for addressing it, and progress on meeting SLAs and risk-reduction goals
How can application risk be mitigated?
Attempting to mitigate all reporting application vulnerabilities is a fool’s errand. The key is to prioritize the application vulnerabilities that pose the greatest risk to your business and to streamline the mitigation process.
Application security risk management solutions are purpose-built to do this. They prioritize application vulnerabilities, orchestrate the remediation process, and communicate risk to a broad set of stakeholders.