Wave Goodbye to the Old Way of Doing Vulnerability Management
Learn MoreStop wasting resources on low risk findings across infrastructure, cloud and application security






Impossible Backlog
Fragmented Visibility
Ownership Complexity
Communications Gap
Millions of vulnerabilities. Dozens of sources. It’s a fool’s errand to try to remediate everything.
How are you prioritizing today?
Hopping from tool to tool. Different definitions of risk. Sounds like an exposure management nightmare. Do you have a single picture of risk across your attack surface?
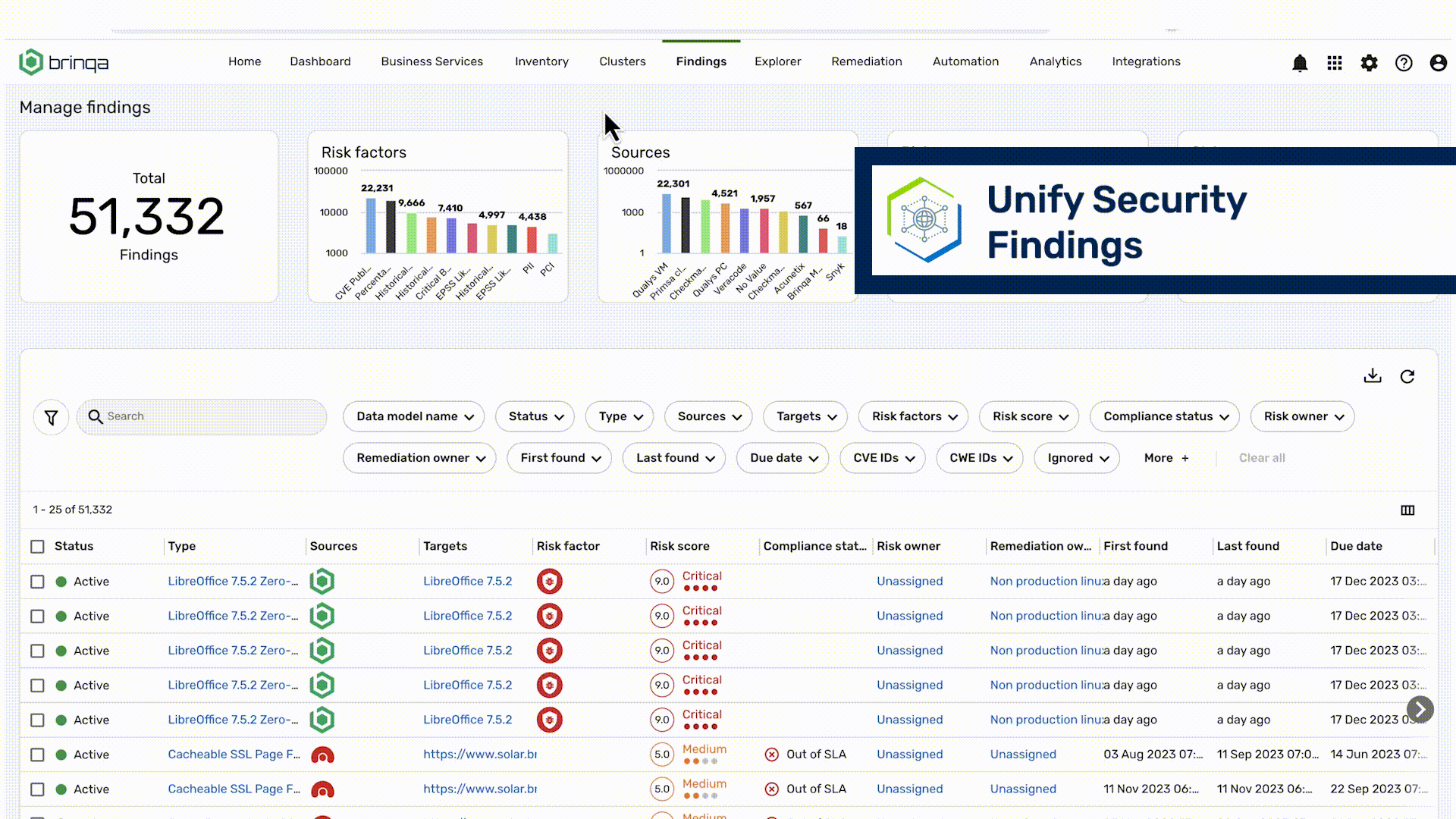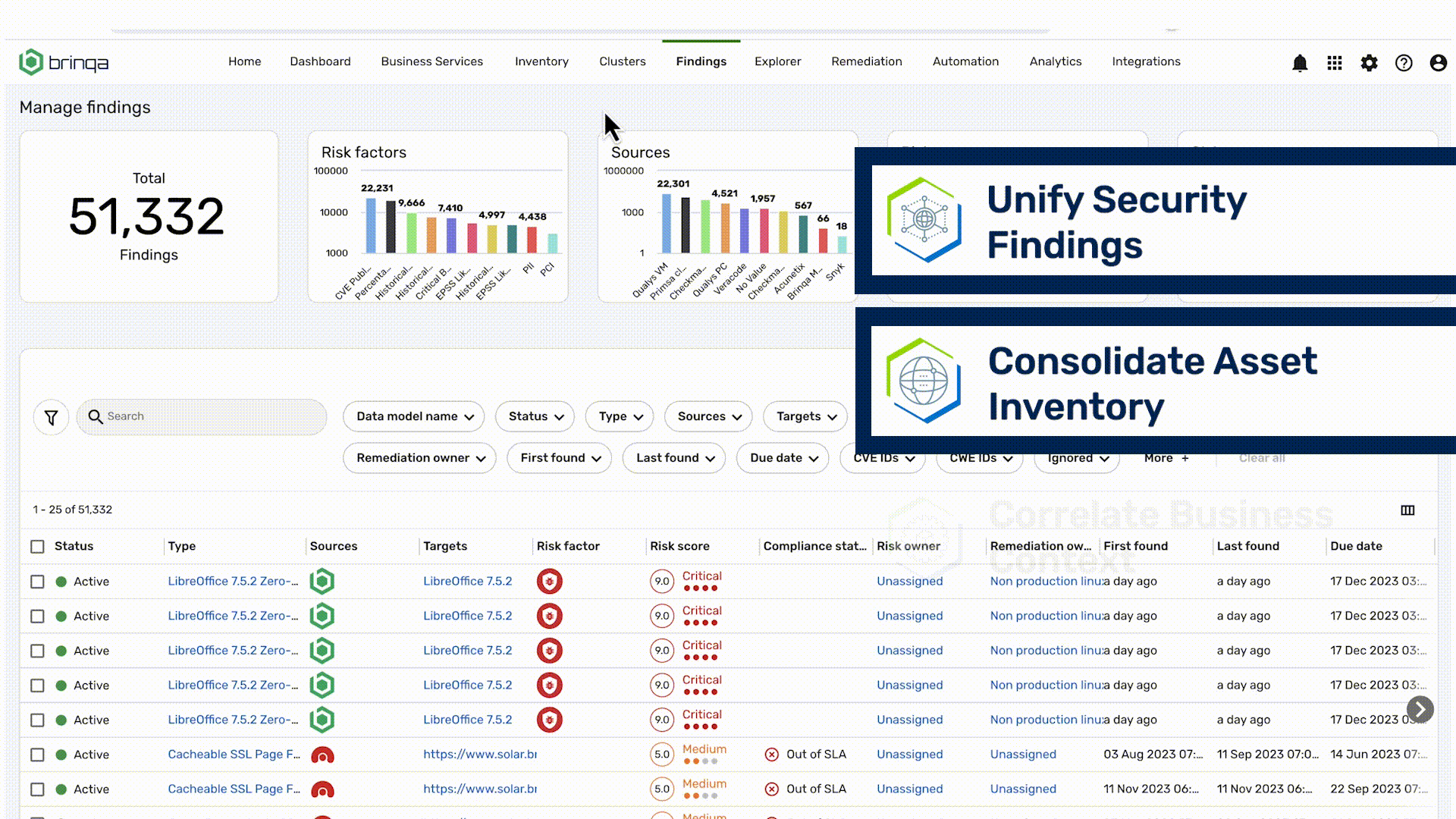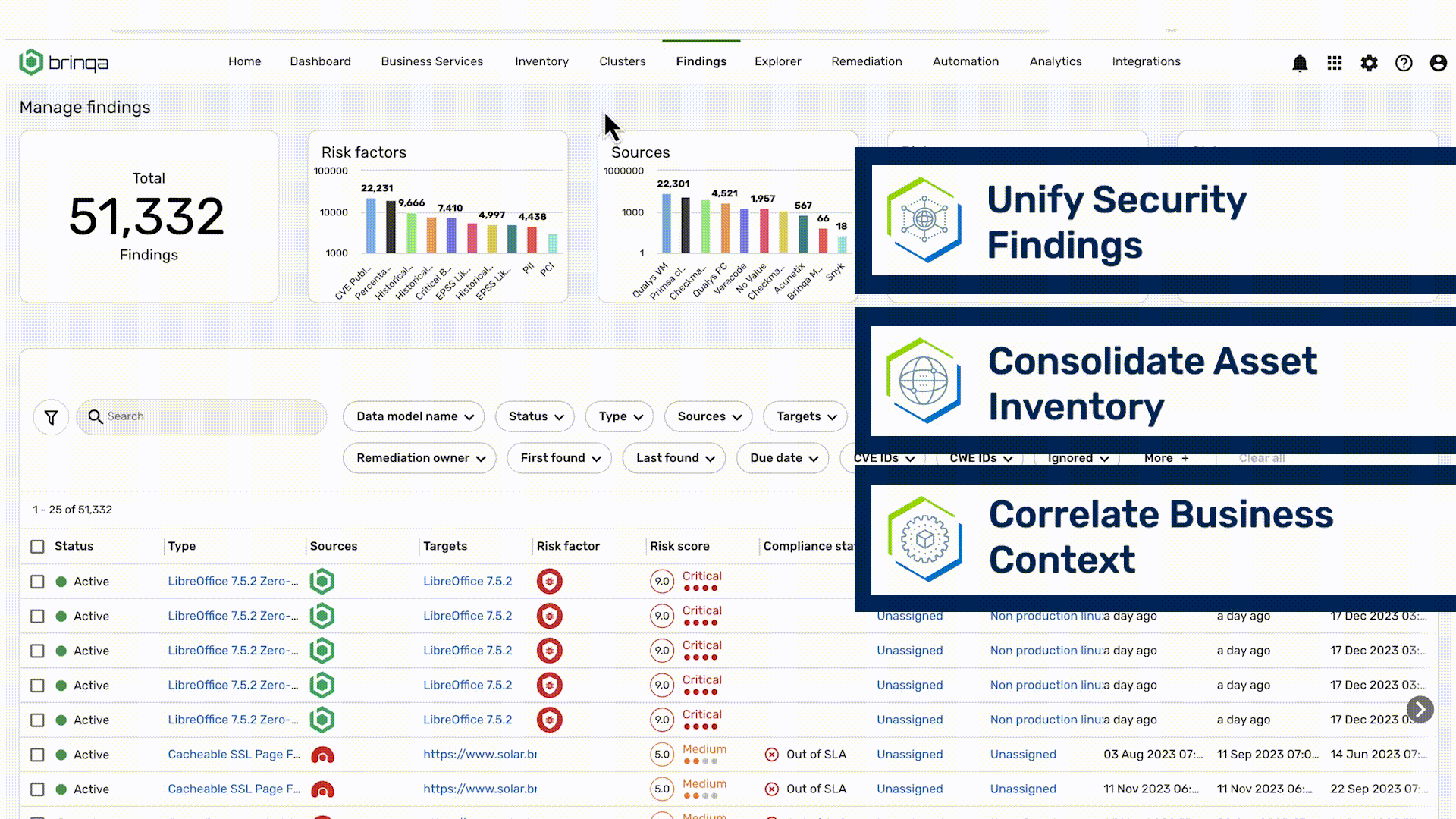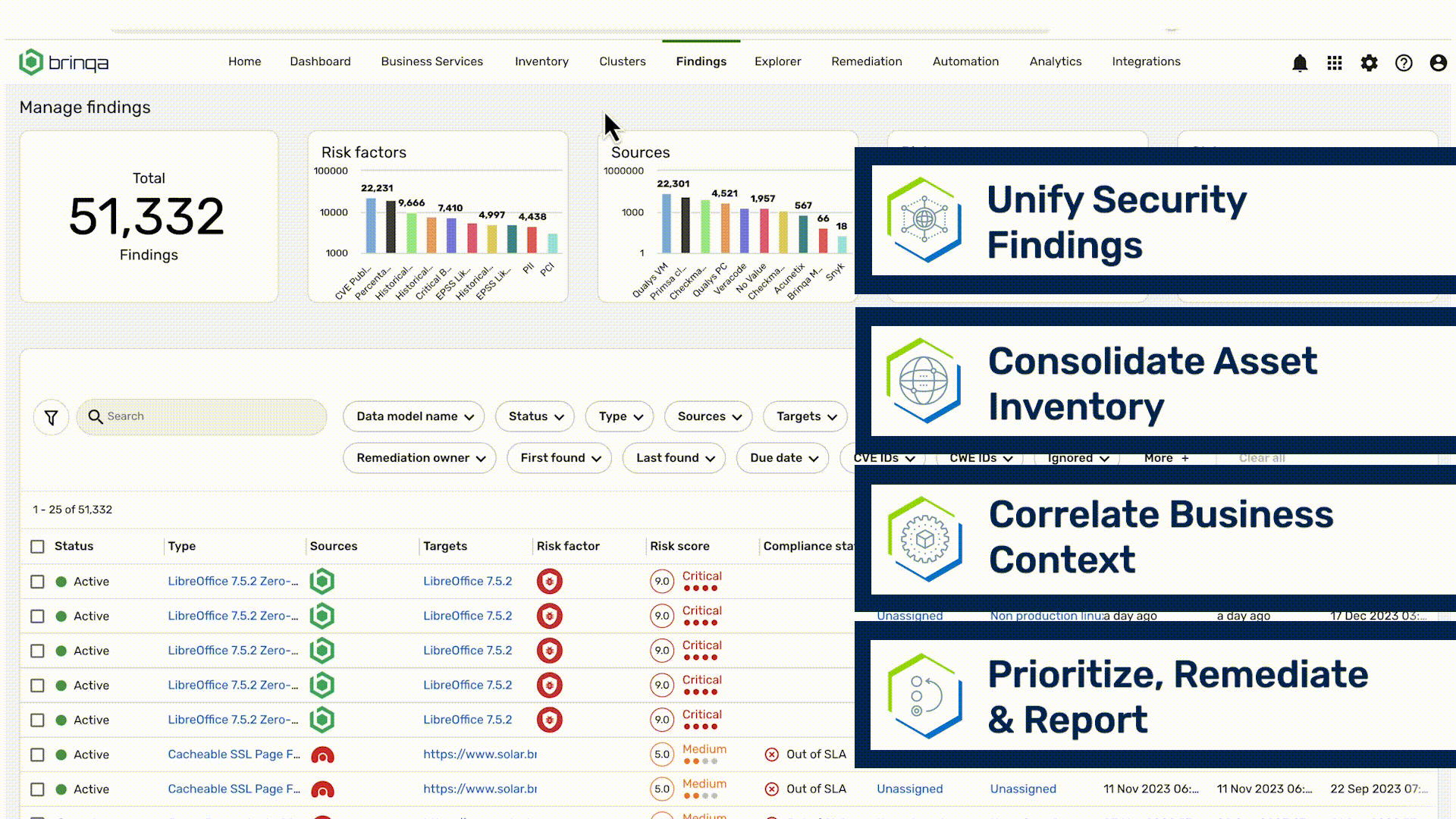
Unify Vulnerability Data
Assets with no owners. Assets with multiple owners. The “who” of remediation is complex. How much time are you wasting trying to find the right owner?
Streamline Remediation
Spreadsheets of CVEs. Lengthy reports. This isn’t motivating non-security stakeholders to act. How do you communicate cyber risk in the context of your business?
Translate Security Speak
Vulnerability management is crumbling under the volume of detected vulnerabilities and mandates to proactively manage cyber risk.
Stop obsessing over detection.
Take a new approach to vulnerability management.
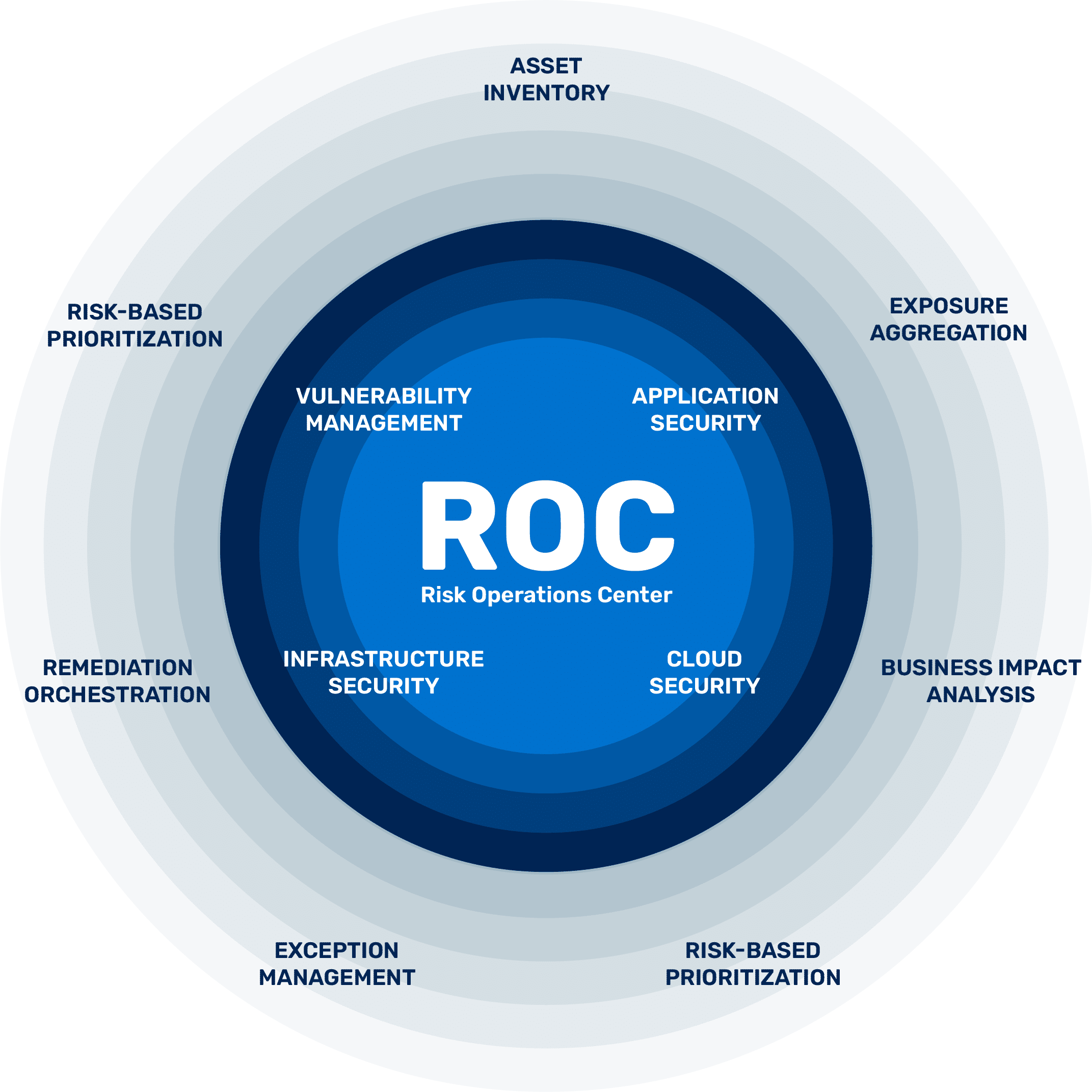
Risk Operations Center
A new approach to managing exposures pre-attack
A Risk Operations Center (ROC) is the heart of a proactive security program. It streamlines workflows for managing and mitigating threat exposures from infrastructure, cloud, application security, and vulnerability management.
This enables CISOs to translate security findings into business impact that executives and boards can understand and act on.
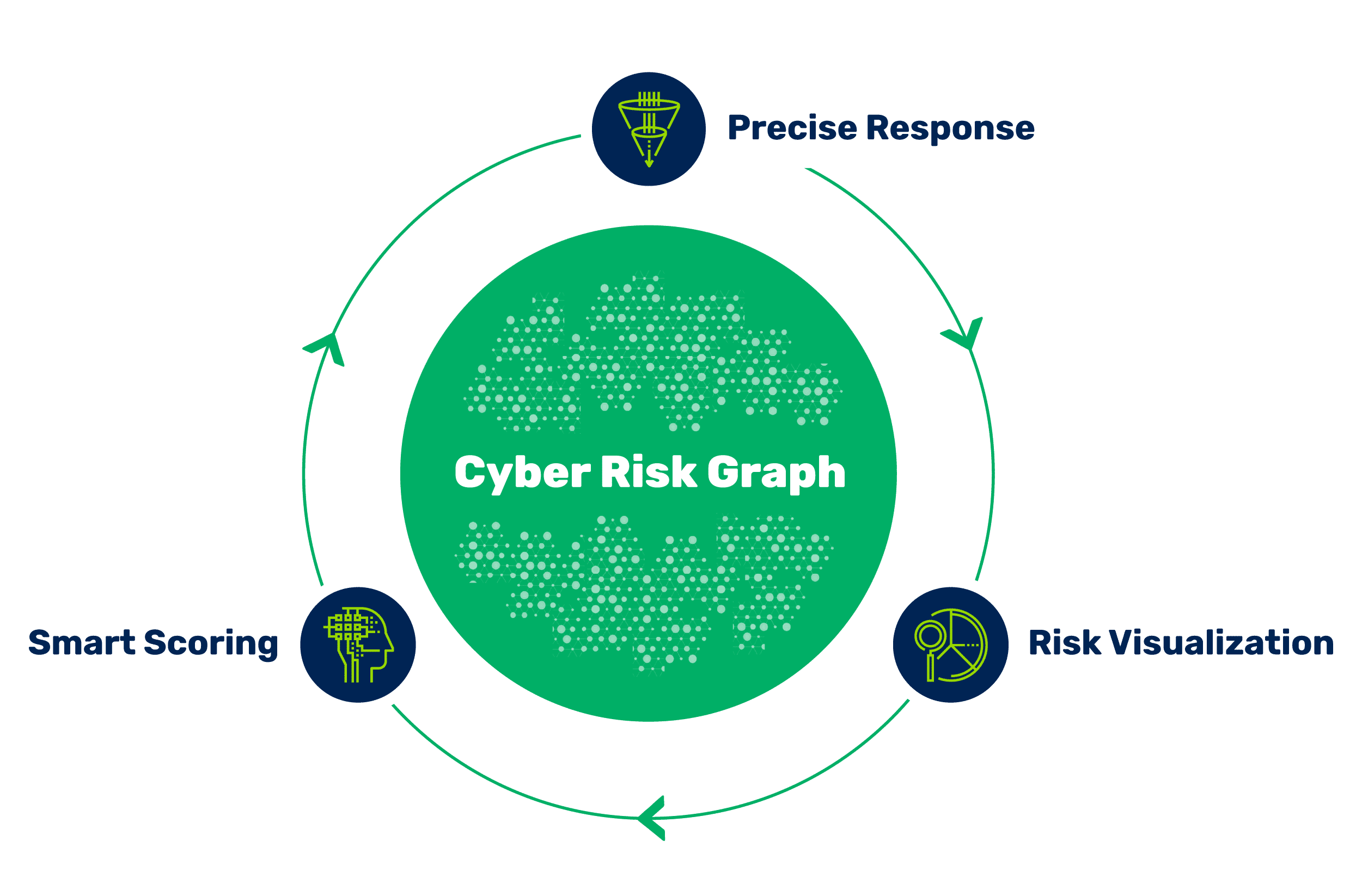
Prioritize infrastructure and cloud vulnerabilities with asset and threat context to streamline your vulnerability management program
For CISOs and security leaders looking to elevate proactive security to manage all exposures pre-attack — enterprise wide
Unify AppSec silos and prioritize security findings across traditional and cloud-native apps to take your program to the next level

Wave Goodbye to the Old Way of Doing Vulnerability Management
Learn More
Risk Operations Center – The New Approach for Proactive Cybersecurity
Learn More
How ASPM is Changing the Game in Application Security
Learn MoreSee Brinqa in action and discover what a modern approach to risk-based vulnerability management looks like.