Brinqa Attack Surface Intelligence Platform
The source of truth for cyber risk across
your security tools, teams and programs
Visualize and understand your entire attack surface
Leverage the full potential of your security tools
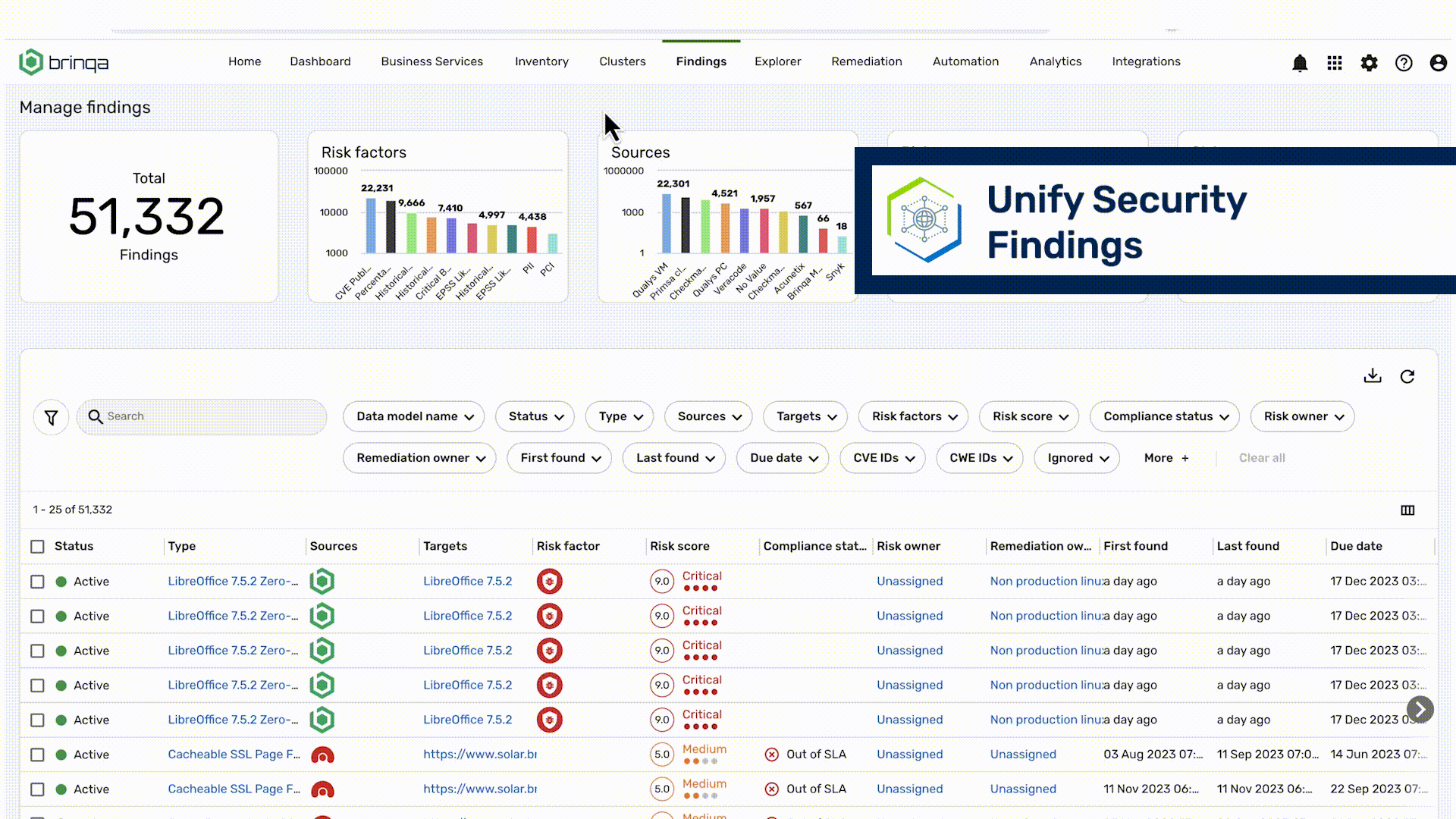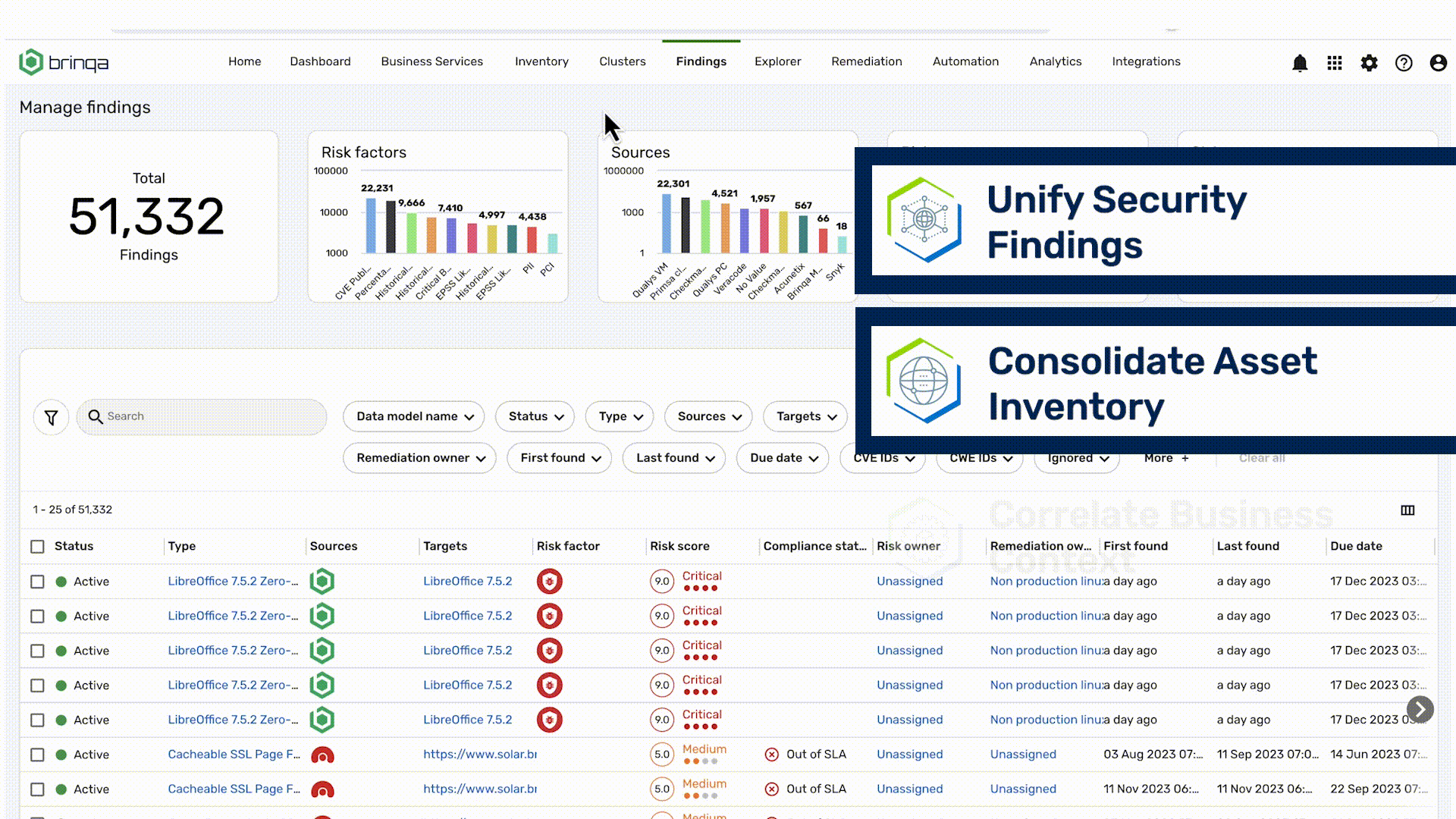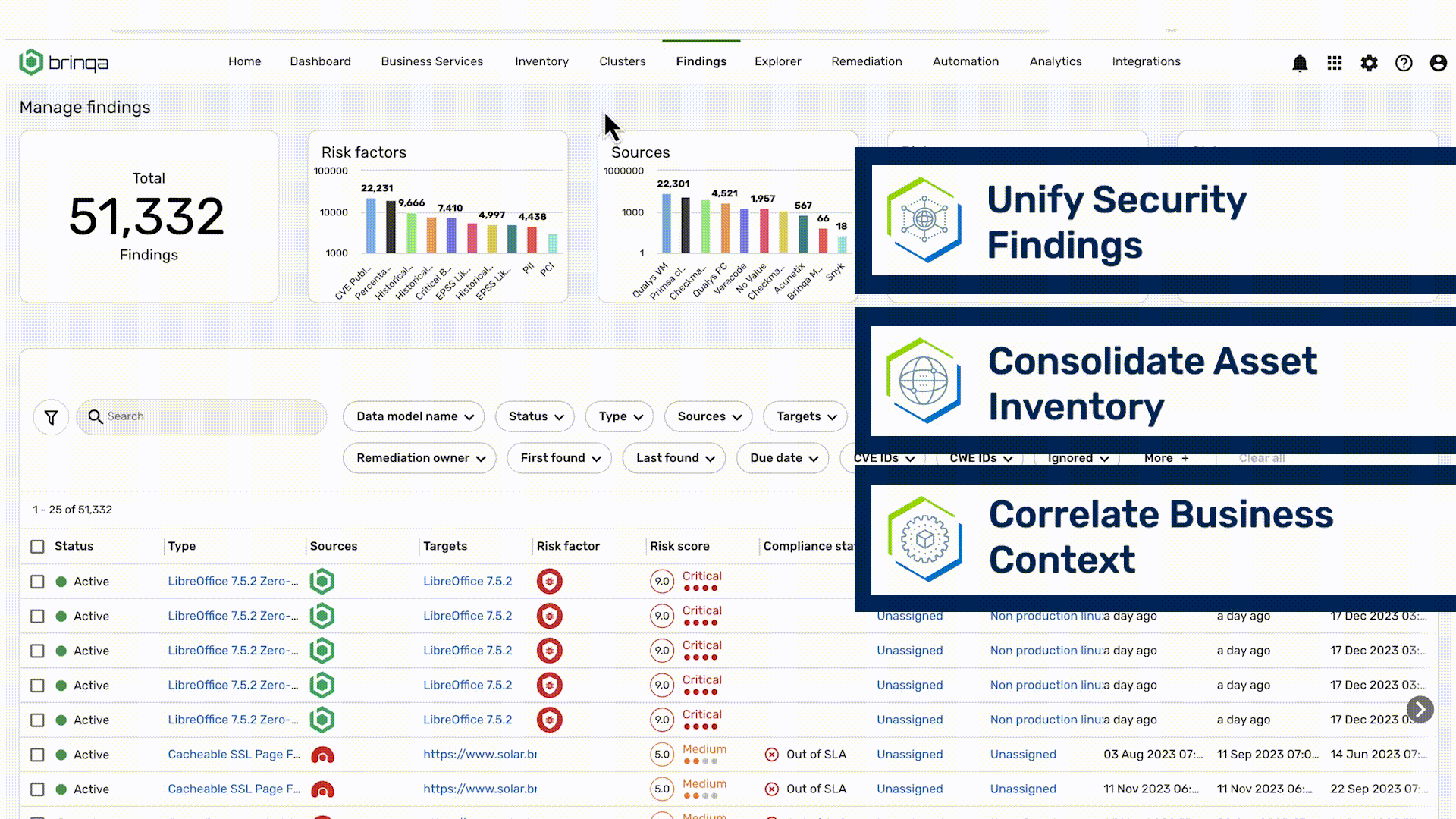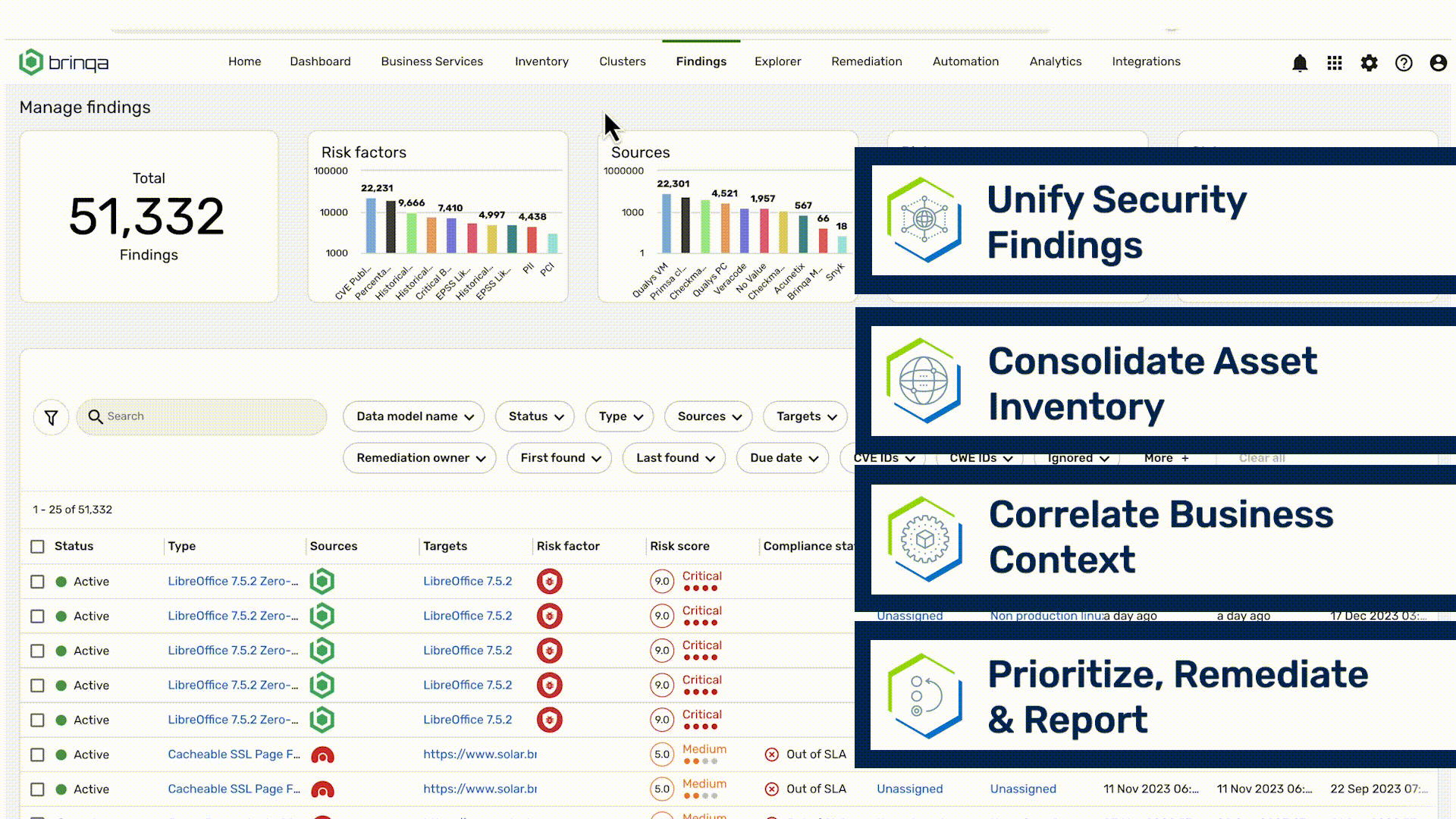
Live Connect integrates 180+ business and security tools to provide a unified inventory of assets and security findings across infrastructure, applications and cloud
- Consolidate asset views into a mega-profile that flags security control gaps
- Collect security findings and normalize vulnerability scores across security tools
- Dynamically sync to reflect changes in your attack surface
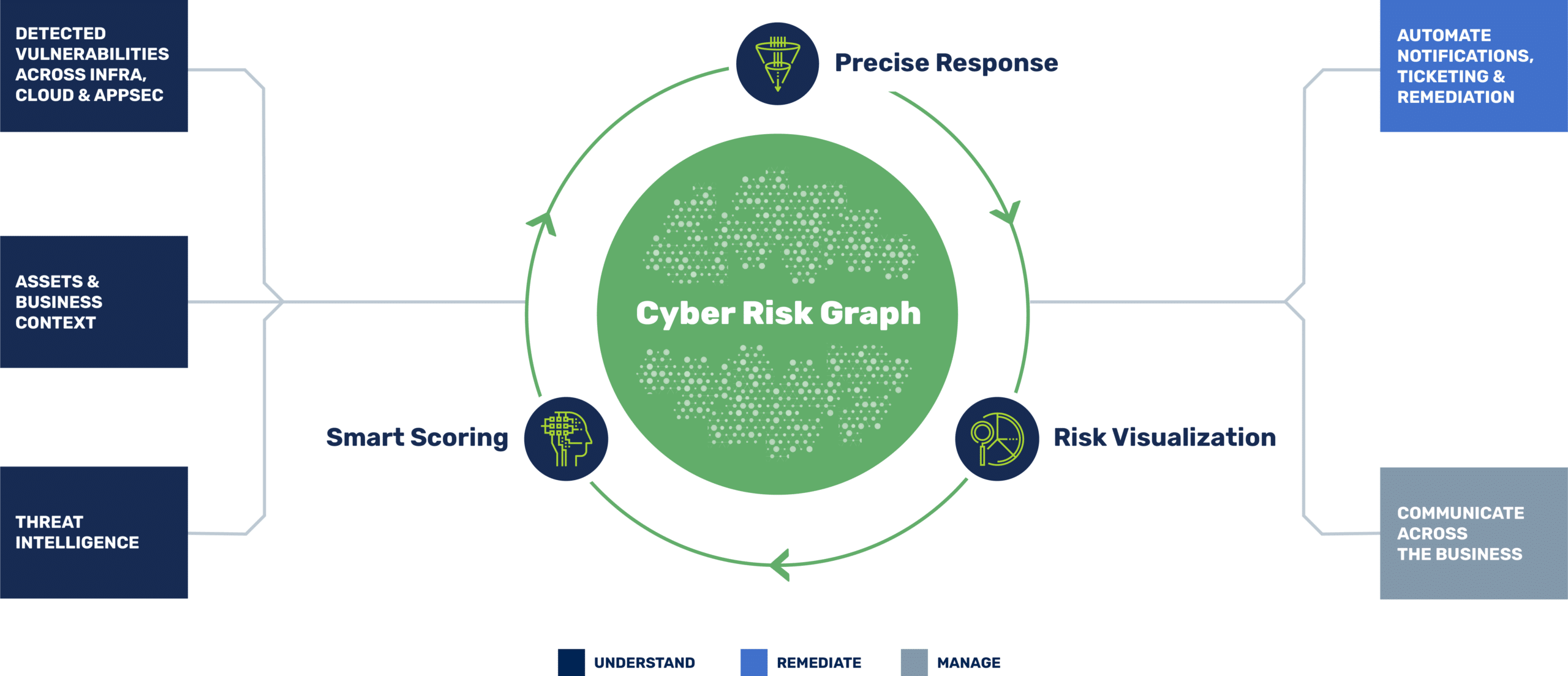
Understand your attack surface like never before
Cyber Risk Graph puts your asset and vulnerability inventory to work by adding business context and threat intel to create a live model of your attack surface
- Understand relationships between assets, findings, controls, ownership, and threat intel
- Add business context and tribal knowledge that ensures your attack surface model reflects your business
- Cluster assets and related risk for tailored perspectives of your attack surface for all stakeholders
Eliminate the risk that poses the biggest threat
Prioritize the risks that matter to your business
Smart Scoring elevates vulnerability scores beyond CVSS with a risk model that understands your attack surface, business priorities, and threat landscape
- Normalize scores from your security tools and apply Brinqa risk scoring best practices
- Enhance scores with Cyber Risk Graph intelligence — relationships between apps, infrastructure, priorities and exploits
- Easily customize resulting scores with unique risk factors specific to your business

Fix high-risk security findings faster with automation
Precise Response orchestrates the remediation and mitigation process by streamlining ticketing, ownership assignment, and closed-loop tracking
- Automate ticketing, notification, validation, exception handling, and SLA enforcement
- Reduce ticket volume by intelligently grouping related vulnerabilities and findings
- Push tickets to the right owners in their tool of choice and validate fixes

Monitor your cybersecurity posture
Communicate risk across the business
Risk Visualization elevates the security conversation with dashboards and reports that reflect business priorities and are easily tailored for all audiences
- Dashboards & metrics track risk from multiple vantage points — vulnerability, asset, app, and business unit
- Motivate action and hold risk owners accountable with risk scorecards
- Provide stakeholders with their own perspective of risk, and it’s all easy to customize

Easily answer the hard questions about cyber risk
Brinqa Query Language gives you quick answers to the deep questions about your attack surface and risk to your business
- A single query language to build dashboards & reports and perform ad-hoc analysis
- Ask complex questions of your Cyber Risk Graph and get quick answers with pre-configured or custom queries
- BQL gives you full access to current and historical risk information for point-in-time and trending analysis

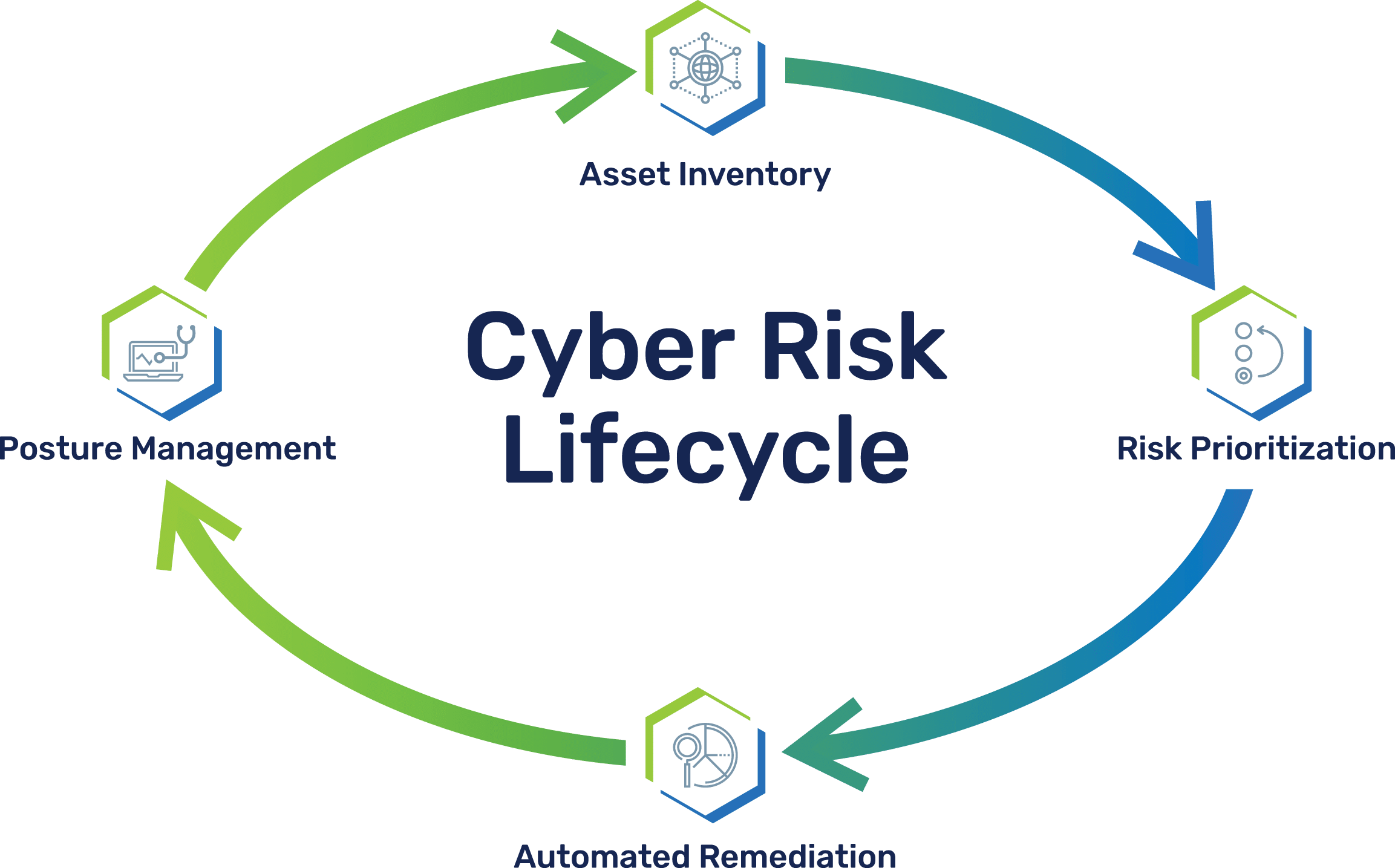
Automate your cyber risk lifecycle
Automate each stage of the cyber risk lifecycle. From scheduling data collection to creating remediation timetables to producing reports, Brinqa gives you the power to create the cyber risk lifecycle that fits your business.
See How We Do It
Experience the power of Brinqa in a short video and see what a modern approach to risk-based vulnerability management looks like.