SOLUTION
Attack Surface Management
Combine unified asset inventory, true risk-based vulnerability management, and effective cyber hygiene

Unified asset inventory of your attack surface
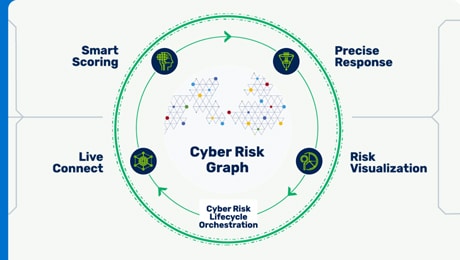
Connect all asset types, threat intel, business context, and security controls into a living model of your attack surface – your Cyber Risk Graph.
Cyber Risk Graph improves security control coverage and establishes definitive ownership through a unified asset inventory that consolidates and enriches profiles per asset.
Risk-based vulnerability management
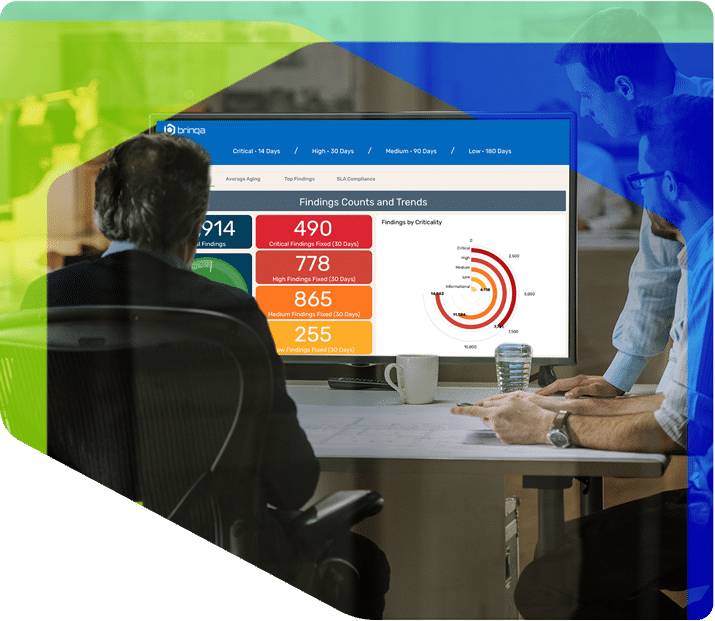
Prioritize the security findings that pose the biggest threats to your business and automate their remediation with a risk model that reflects business priorities and likelihood of exploit.
Making your cybersecurity programs risk-based transforms simple vulnerability scores into a company-wide view of threats to focus teams on fixing what matters.

Cybersecurity hygiene
Strengthen your security posture by continuously evaluating cyber hygiene across your attack surface to detect security control coverage gaps and report on security program effectiveness.
Easily answer questions about the most complicated security controls — are they being applied across my entire attack surface, and are they working?

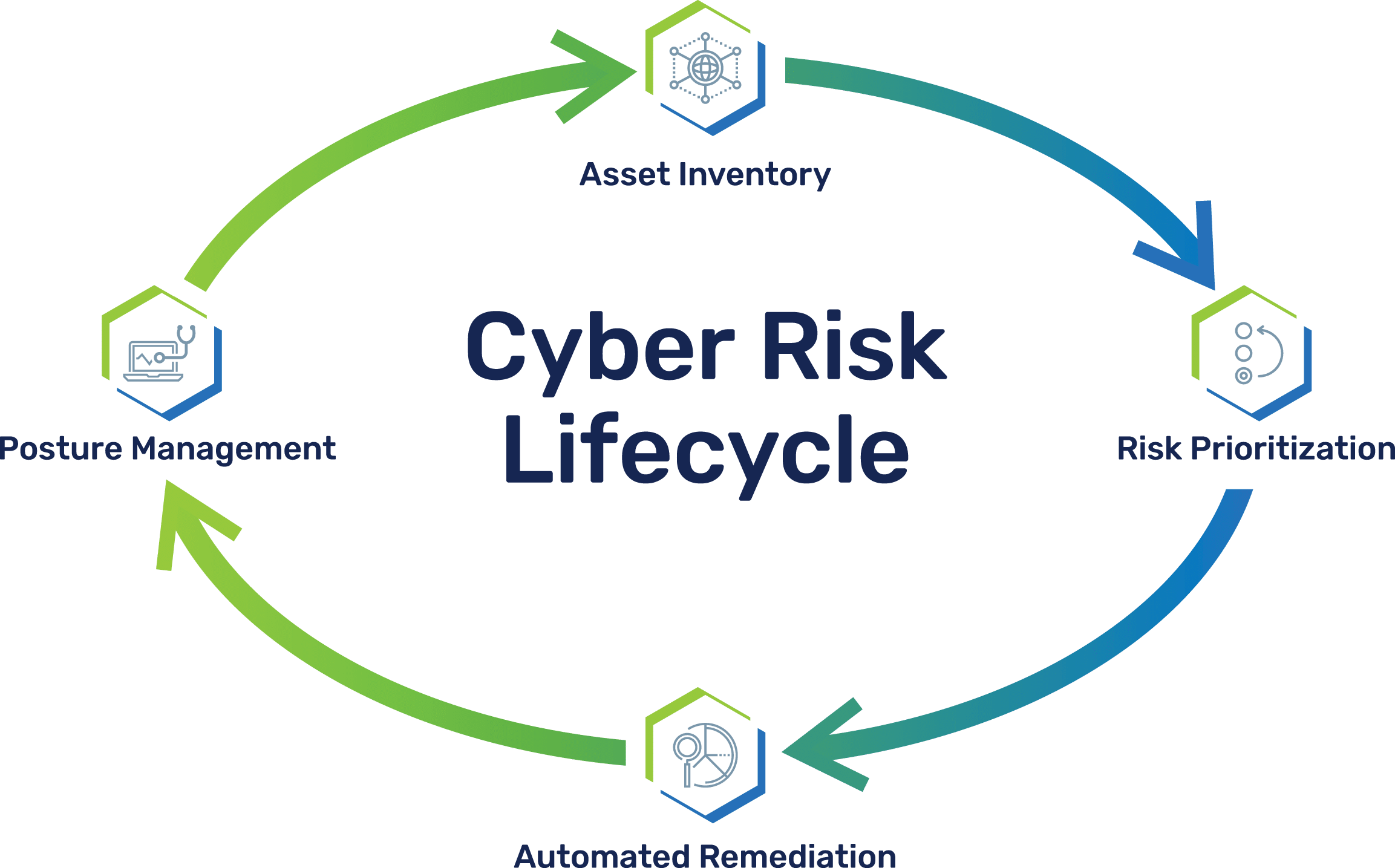
Unify asset & vulnerability inventories, reduce risk, manage hygiene
Brinqa provides one platform to establish a single source of truth for assets and their vulnerabilities that powers multiple use cases — all to reduce your attack surface
Experience the true power of the Brinqa platform in a demo.
Request Demo