Wave Goodbye to the Old Way of Doing Vulnerability Management
Learn MorePrioritize infrastructure & cloud vulnerabilities using asset and threat data to streamline your vulnerability management program

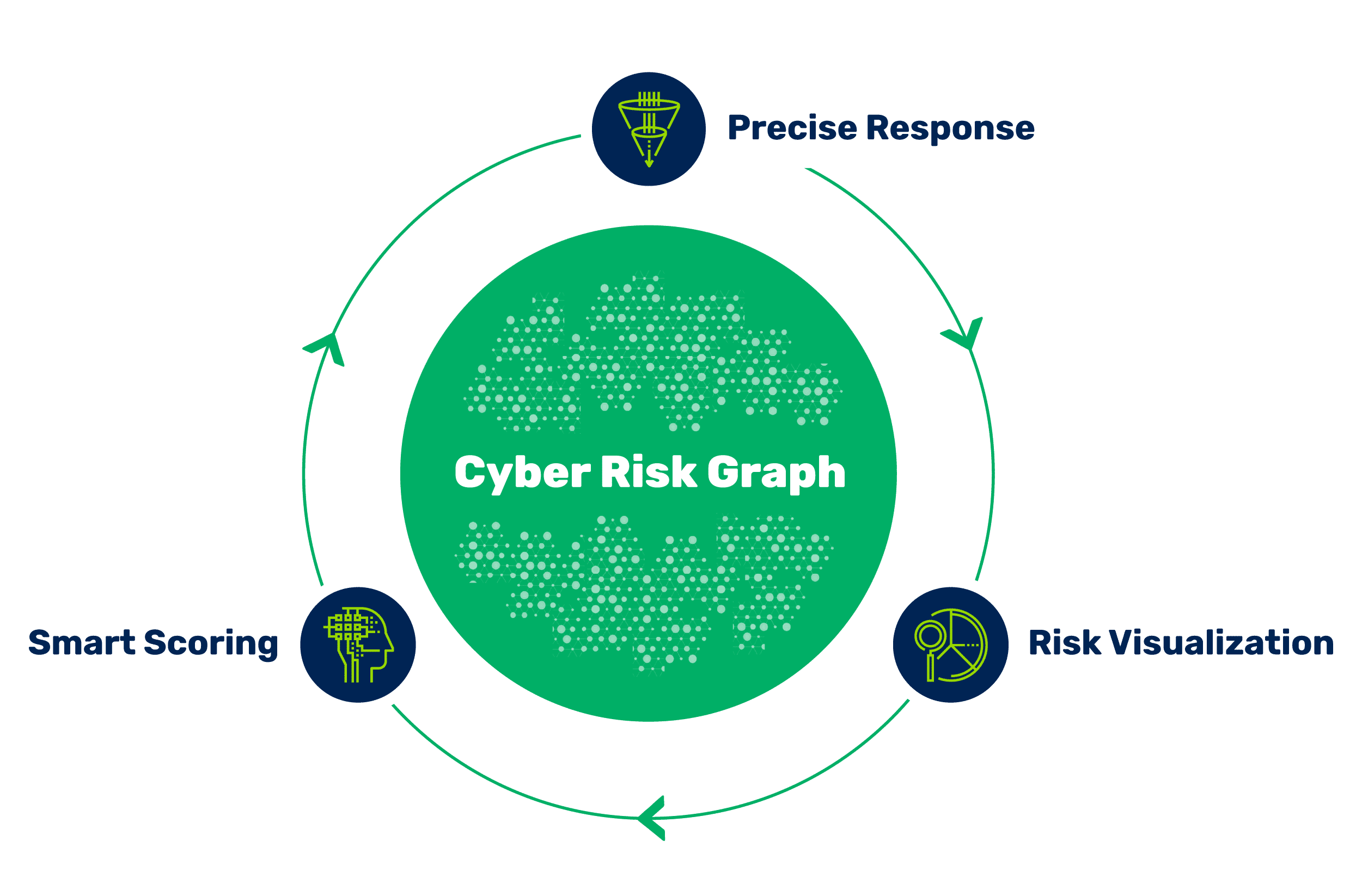
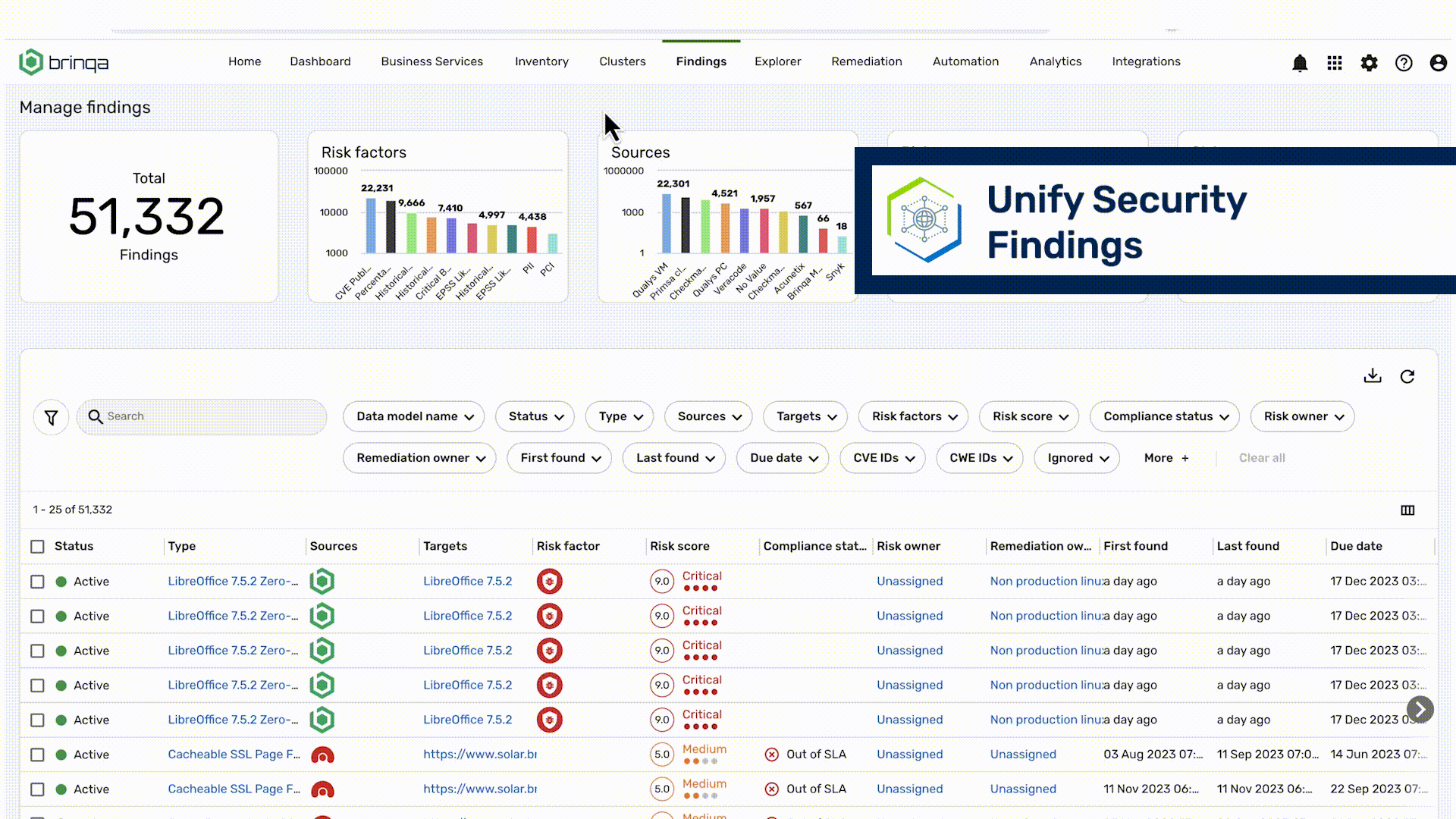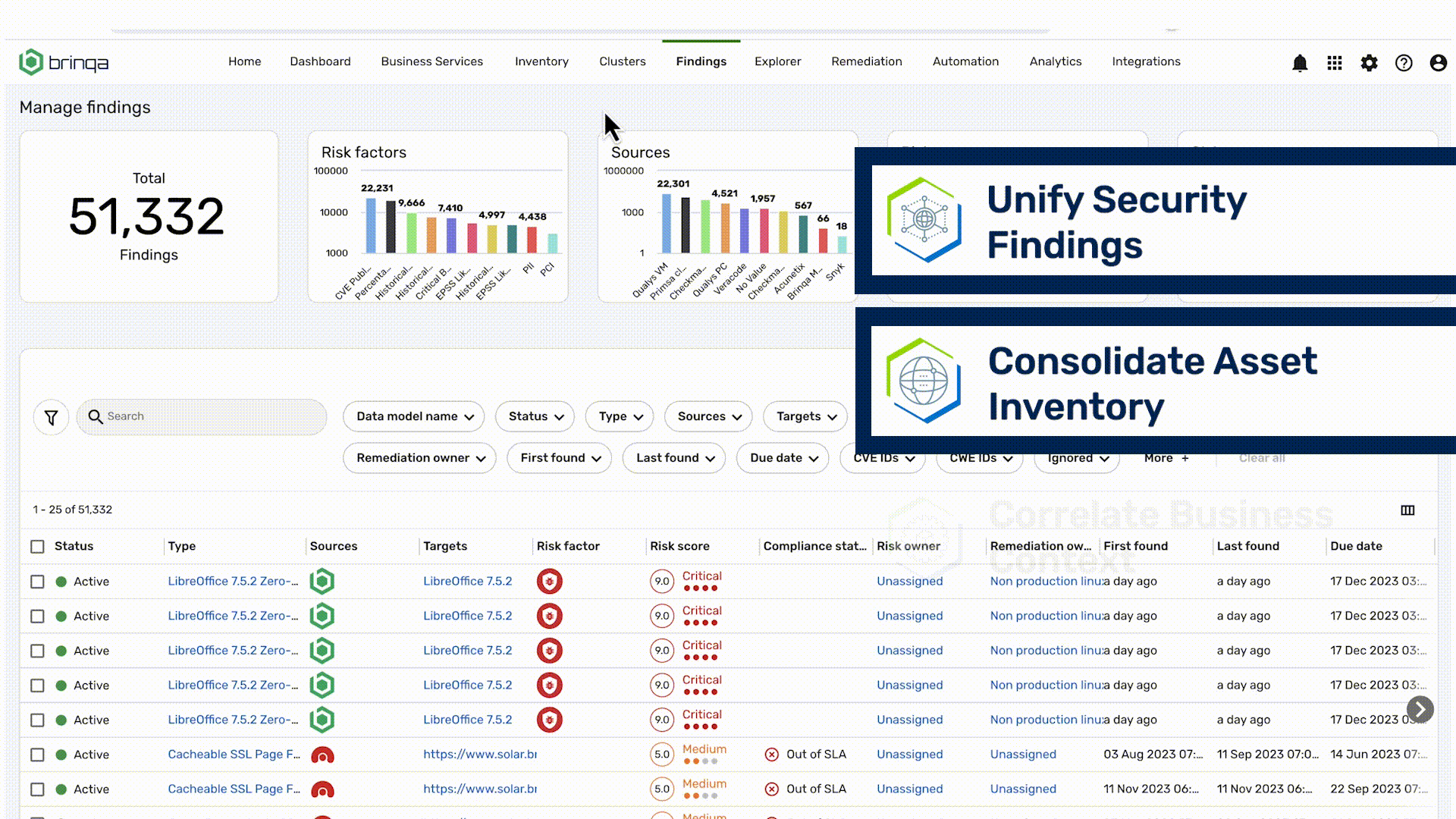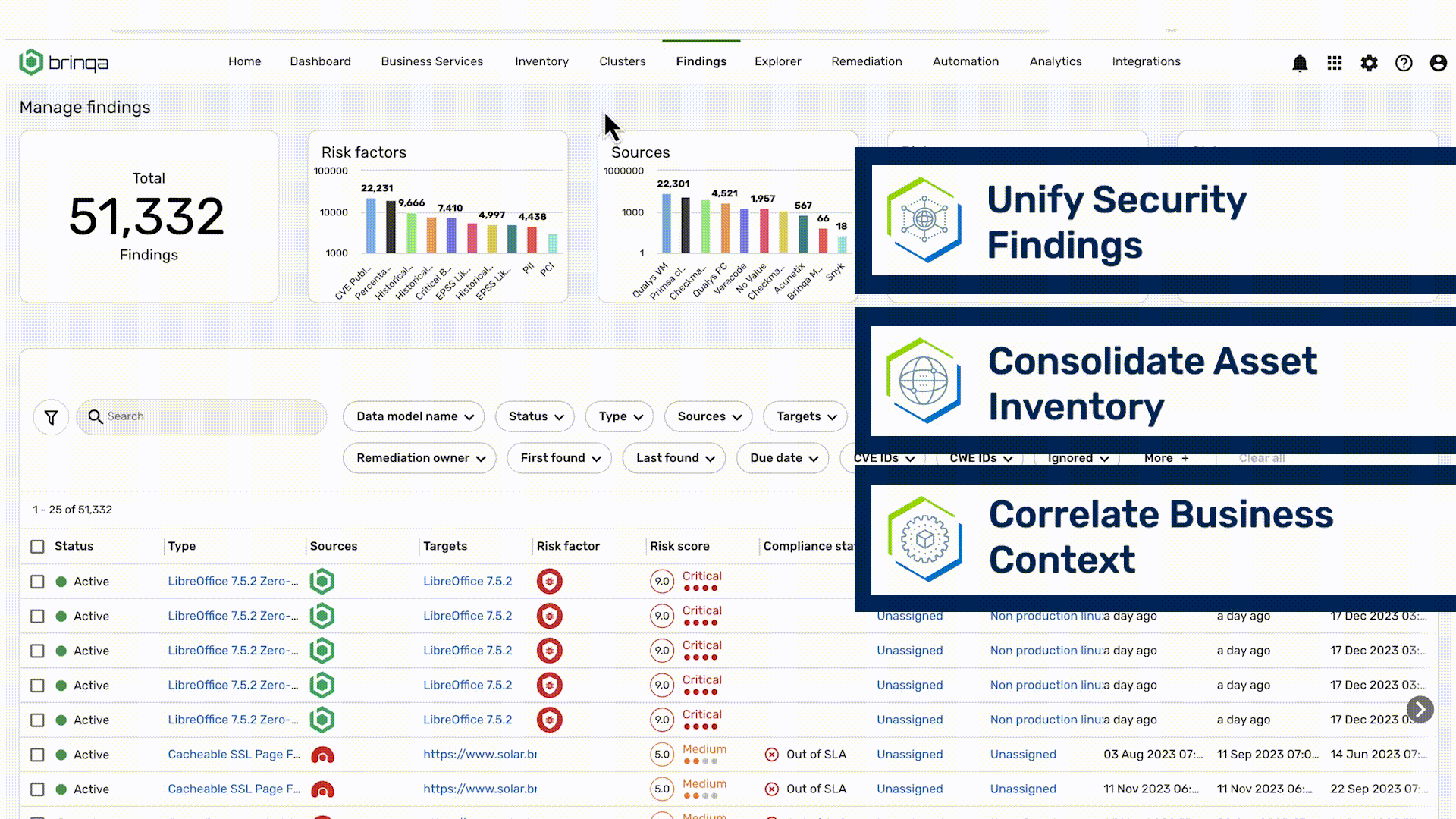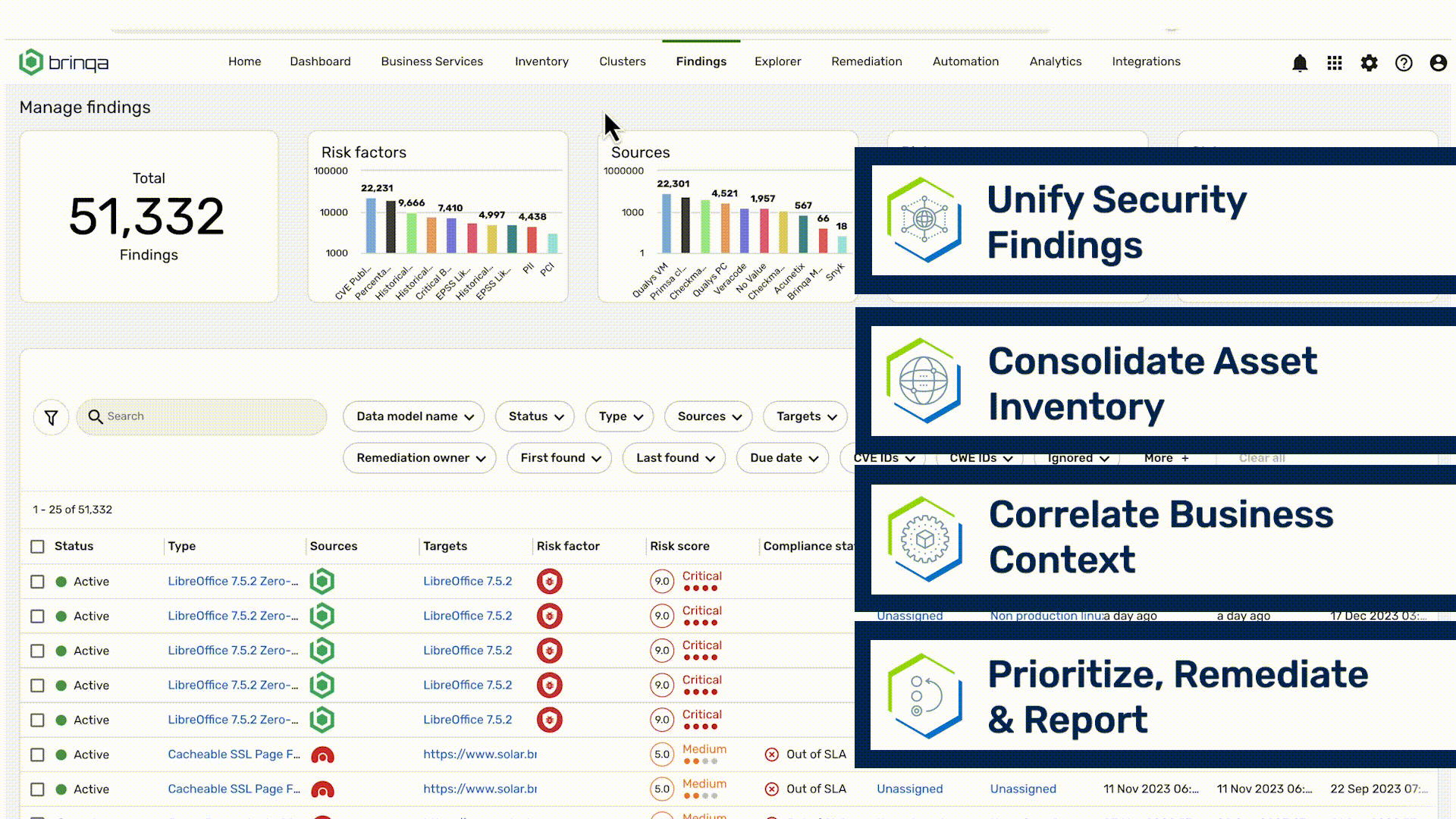
Instantly filter through the millions of vulns distracting your teams. Go beyond CVSS with risk scores automatically tailored to your business with context from your assets, existing security controls, and more.
Hopping from tool to tool doesn’t get you the full picture of assets and their vulnerabilities. Get an instant understanding of risk with a unified view across your traditional and cloud infrastructure.

Fix high-risk findings fast with automated ticket creation, owner assignment, notifications, and validation. Create workflows for risk acceptance, false positives and exception requests.
If you can’t get business and remediation teams to understand and act, the rest doesn’t matter. Tailored analytics for security, remediation, and business teams turns random acts of security into precise risk reduction.






“We achieved a 90% reduction in critical vulnerabilities and a 75% reduction in high-severity vulnerabilities with Brinqa.”

Wave Goodbye to the Old Way of Doing Vulnerability Management
Learn More
Ungated Gartner Report: How To Implement a Risk-Based Vulnerability Management Methodology
Learn More
See Brinqa in action and discover what a modern approach to risk-based vulnerability management looks like.
Vulnerability assessment is the process of identifying, quantifying and prioritizing vulnerabilities in the software, hardware, cloud, and on-premises assets that make up an organization’s attack surface.
Vulnerability management is the operational practice of identifying, classifying, remediating and mitigating vulnerabilities across an organization’s attack surface.
Risk-based vulnerability management is the process of prioritizing, remediating and reporting on vulnerabilities based on the risk they pose to the business.
Traditional vulnerability management lacks the business context and threat intelligence to prioritize vulnerabilities based on the risk they pose to the specific business. Too often, vulnerability management programs rely solely on CVSS scores or scanner results to assign a priority, leaving security teams drowning in vulnerabilities and application and operations teams frustrated by chasing down and fixing vulnerabilities that don’t matter.
The objectives of a vulnerability risk management program are to identify, prioritize, communicate and remediate only the vulnerabilities that matter to the business.
A well-run risk-based program delivers the following benefits:
A risk-based approach enables the business to reduce the right cyber risks fast, while minimizing business disruption.