Implementing CTEM at Scale
The Challenges of CTEM, and What It Takes to Power It
The Brinqa Solution
How Brinqa Powers a CTEM Strategy

The Brinqa Solution
How Brinqa Powers a CTEM Strategy
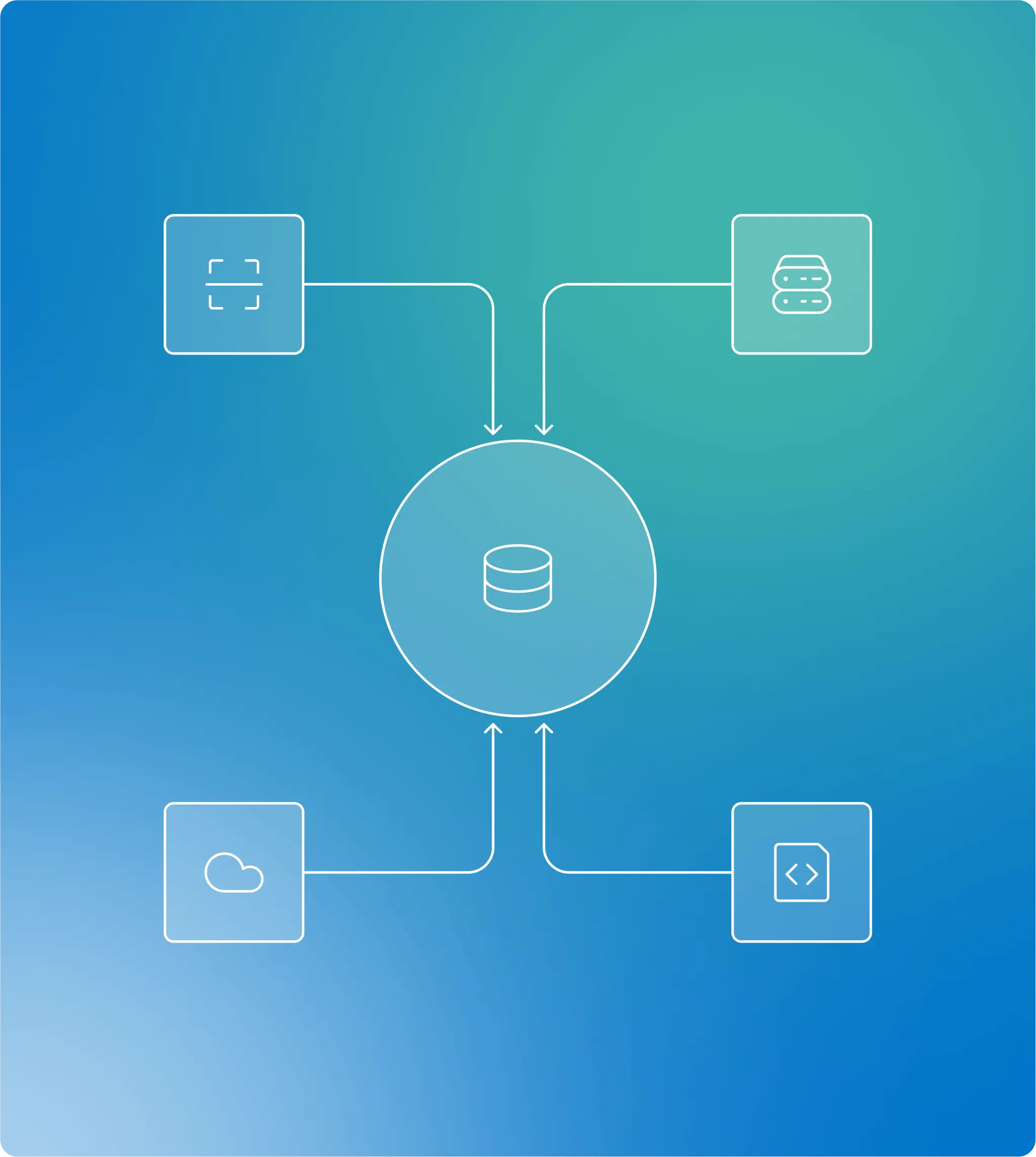
Brinqa operationalizes CTEM by connecting the tools teams already use into a single, data-driven platform. With 240+ out-of-the-box integrations, Brinqa brings together asset, vulnerability, threat, and business data to give teams deeper visibility, richer context, and a clearer view of real exposure.
By using more of this data—not just isolated findings—Brinqa correlates signals across sources to support better decisions and faster, more targeted remediation. Teams maximize the value of existing security investments while moving CTEM from a framework into a repeatable, scalable practice.
Key Capabilities
Orchestrating Risk Reduction Across the CTEM Lifecycle
Brinqa integrates with 240+ security, IT, cloud, and business tools to create a unified asset and exposure inventory, mapping relationships across assets, findings, ownership, and business context.

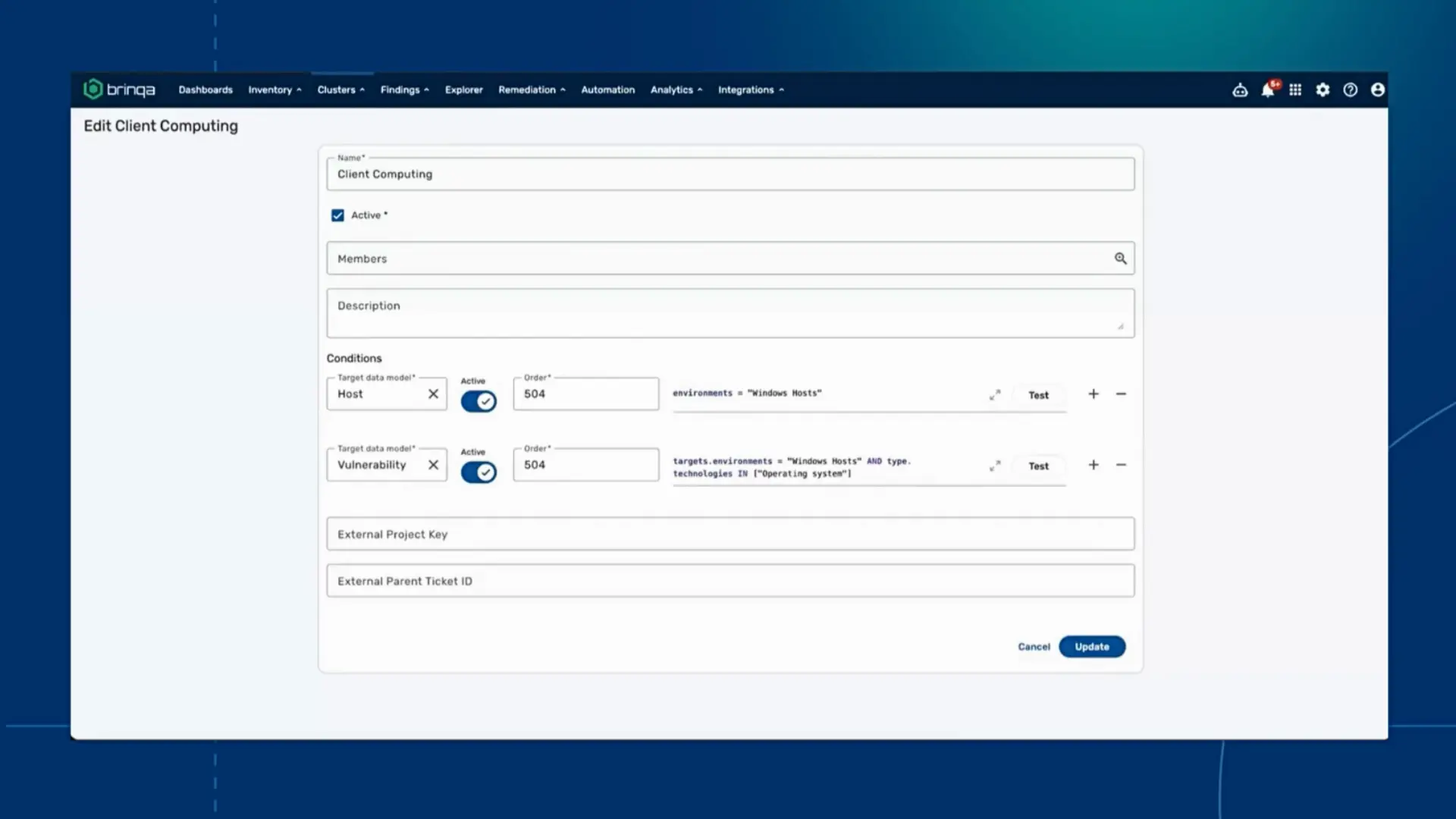
Identify & Target Remediation Owners
See how Brinqa operationalizes mobilization
Watch how Brinqa automatically assigns remediation ownership at the layer level — turning CTEM’s mobilization stage into coordinated action across teams.
Why Brinqa
Discover Key Features That Deliver an Enterprise Level Strategic Edge
Customer Success Stories
Proven Enterprise Outcomes
Brinqa at Work
Solutions For Every Member of Your Vulnerability Management Program
CISOs and security risk leaders

Exposure and risk management teams

Security Operations Teams


Exposure Management
The CTEM Challenge: Too Many Tools, Not Enough Integration

