How AI Is Supercharging Unified Vulnerability and Exposure Management

A Pragmatic Roadmap for Adopting AI for UVEM
Artificial intelligence has emerged as a transformative force in cybersecurity. From machine learning models that detect anomalies to generative AI that enables conversational interfaces, the adoption of AI is enabling faster, more precise decision-making.
AI has expanded what’s possible in vulnerability and exposure management too — democratizing access to insights and accelerating remediation. These outcomes are especially relevant as organizations move beyond siloed vulnerability scanning and toward unified vulnerability and exposure management (UVEM), exposure assessment platforms (EAP), and ultimately continuous threat exposure management (CTEM) – a journey that demands greater speed, scale, and precision which can be sustainably delivered with an AI-first approach.
Adopting AI to complement UVEM use cases requires a pragmatic approach aligned with business outcomes. This post explores key considerations and use cases to maximize AI use in UVEM.
Top AI Considerations: Data Quality and Interface
The effectiveness of any AI system is only as strong as the data it operates on. A comprehensive, continuously updated data lake is the foundational layer upon which meaningful AI capabilities are built. Solutions that include a data-centric foundation that unifies and enriches risk data across the enterprise — from cloud to on-prem to hybrid environments – will ensure that AI-powered insights and workflows are both accurate and actionable.
Equally important to the data behind the AI model is how easy it is to interact with it. That’s where natural language interfaces shine, offering contextual, governed AI interactions that make cybersecurity data accessible and usable for a wide range of personas — from security analysts to executive stakeholders.
AI Use Cases for Unified Vulnerability and Exposure Management
Security and vulnerability management teams face continued challenges in managing their complex environments. The adoption of AI within UVEM is solving these challenges head-on.
Integration
Most enterprises leverage dozens of vulnerability and exposure data sources, and these tools generate millions of vulnerabilities and alerts often viewed in silos. AI-enhanced data normalization deduplicates across sources for cleaner, more reliable data and speeds up integrations across new data sources.
Smarter Vulnerability Prioritization
To accurately prioritize risk, security teams need to understand the relationship between vulnerabilities, assets, and business functions. AI supercharges advanced UVEM prioritization capabilities by analyzing exploit data, asset exposure, business importance, and threat intel to surface the vulnerabilities most likely to be exploited in your environment.
Threat Enrichment
New exploits emerge rapidly. Traditional systems can’t react in real time, leaving organizations exposed. AI-based real-time threat enrichment can identify emerging attack patterns across open-source intel, dark web chatter, and exploit kits — and influence risk scoring often before vulnerabilities are weaponized.
Remediation & Workflow Automations
Security teams are overwhelmed, so effective prioritization is critical to doing more with less. AI can recommend optimal remediation paths based on historical effectiveness, business constraints, and urgency. From ticketing to patch orchestration, AI supports adaptive remediation workflows that accelerate risk reduction.
How to Pragmatically Adopt AI in Your UVEM Program
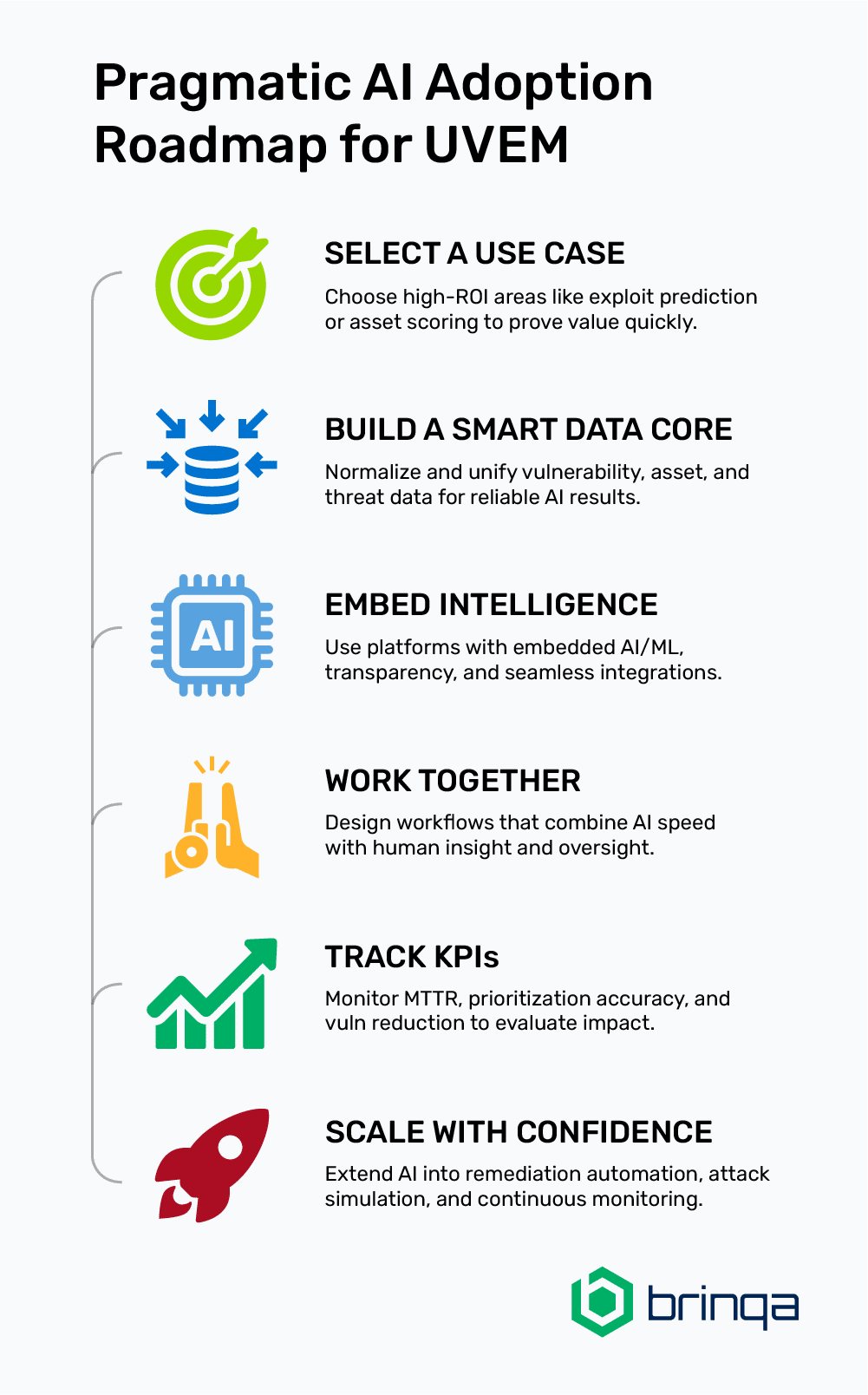
- Start with a Specific Use Case: Target areas with high ROI, such as exploit prediction or asset scoring. Get a win, then scale.
- Ensure Clean, Connected Data: AI’s output is only as good as its input. Consolidate and normalize your vulnerability, asset, and threat data.
- Pick Tools with AI at the Core: Look for platforms with embedded AI/ML, explainability, and seamless integrations with your existing tech stack.
- Build for Human + Machine Collaboration: Design your workflows to combine AI speed with human judgment.
- Measure Results: Track KPIs like Mean Time to Remediate (MTTR); reduction in critical open vulns; accuracy of prioritization; and false positive rate over time to demonstrate the value of additional AI capabilities above and beyond UVEM.
- Scale Thoughtfully: Once early success is achieved, extend AI into areas like automated remediation, attack simulation, and continuous exposure monitoring.
AI in Action
AI has the potential to dramatically improve the speed, accuracy, and impact of UVEM — helping organizations stay ahead of threats while making the most of limited security resources. But it’s not magic. The key is starting small, choosing the right problems, and layering AI into your program in a way that’s explainable, trustworthy, and aligned with your business goals.
Want to see AI-driven UVEM in action? Request a demonstration of the Brinqa unified vulnerability and exposure management platform to explore how your team can shift from vulnerability overload to intelligent, risk-based decision-making — powered by AI.
Frequently Asked Questions
What is Unified Vulnerability and Exposure Management (UVEM)?
UVEM refers to a unified, risk-based approach that consolidates vulnerability and threat data across environments (cloud, on-prem, hybrid) to deliver contextual, prioritized, and actionable insights — enabling faster, more effective remediation.
How does AI complement vulnerability and exposure management?
AI complements UVEM by automating data correlation, identifying exploit patterns, prioritizing vulnerabilities based on real-world risk, and recommending remediation actions — all at a scale and speed that humans alone can’t match.
What are the top AI use cases in UVEM?
- Integration and deduplication across data sources
- Smarter vulnerability prioritization
- Real-time threat enrichment
- Remediation recommendations and workflow automation
What types of AI are used in UVEM platforms?
UVEM platforms may use various AI types including:
- Machine learning for pattern recognition and predictions
- Natural language processing (NLP) for search and reporting
- Generative AI for conversational interfaces and contextual insights
What are the biggest risks of using AI?
Key risks include:
- Lack of transparency (“black-box” decisions)
- Bias or gaps in training data
- Overreliance on automation
- Inaccurate or stale data inputs
These can be mitigated through explainable AI, diverse datasets, human oversight, and continuous data enrichment.
Why is data quality so important for AI in UVEM?
AI models are only as good as the data they process. Clean, enriched, and continuously updated data ensures accurate predictions, reliable prioritization, and effective automation — without introducing risk or noise.
How does generative AI enhance vulnerability management?
Generative AI enables conversational interfaces that make cybersecurity data more accessible to non-technical users. It also helps accelerate reporting, decision-making, and insight delivery across teams.
How do I start implementing AI in my UVEM program?
Start small with a focused use case like exploit prediction or asset criticality scoring. Ensure your data is clean and connected, select AI-capable tools, and build workflows that support human + machine collaboration.
How do I measure the success of AI in UVEM?
Key metrics include:
- Mean Time to Remediate (MTTR)
- Reduction in critical or exploitable vulnerabilities
- Accuracy of prioritization
- False positive/negative rates
- Speed of remediation workflows