How to Increase Vulnerability Remediation Effectiveness

Want to identify your best ROI opportunities for improving the operational efficacy of your vulnerability remediation efforts?
When I say operational efficacy, I’m talking about determining the overall effectiveness of your vulnerability management program.
Start by comparing the rate at which your team identifies vulnerabilities to the rate at which you prioritize and address them. Doing this enables you to work smarter to reduce the most significant number of risks using your existing resources. That means you know — and can defend — where you focus your limited resources.
In the broadest sense, you add up the number of findings all of your scanners provide and compare it to the number of vulnerabilities noted as remediated/addressed over a given period. Take this concept and filter it down as it makes sense for your organization. Looking at critical vulnerabilities found vs. remediated may make more sense for you. Or, you could consider the efficacy related to your most critical assets.
You get the idea. Apply this ratio however it best works for your organization. Here are three scenarios to take you through the process.
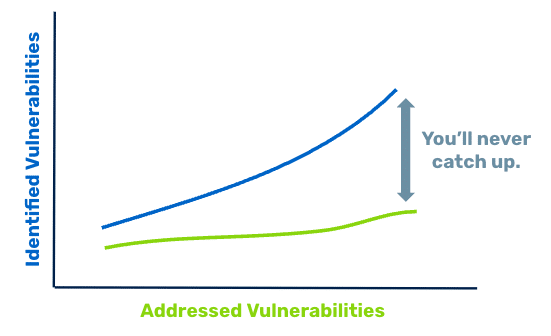
The “Catch Me If You Can” Scenario
If you’re finding more vulnerabilities than you are addressing, it’s time to rethink your approach.
The “Treading Water” Scenario
If you’re addressing as many vulnerabilities as you are finding, don’t celebrate prematurely.
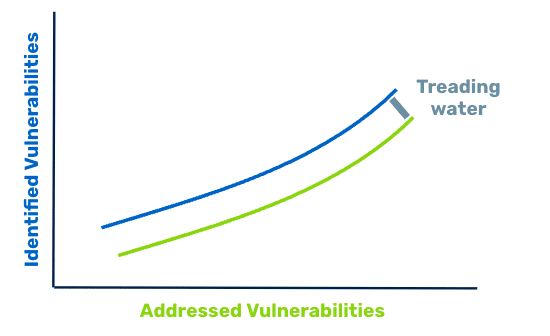
If you’re breaking even addressing your findings, you won’t ever catch up, which is a sign you need to improve the processes that address already-known vulnerabilities. You’ll achieve a higher return on your efforts by improving processes rather than adding more findings from more scanners to the pile.
The “Don’t Stop Believin'” Scenario
If you’re addressing more vulnerabilities than you find, it’s a sign of program maturity, but don’t stop there – the journey has just begun.
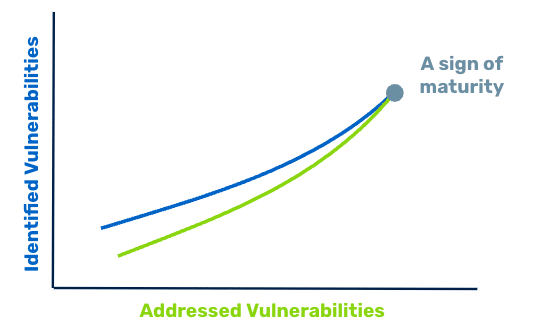
Congratulations! You’ve entered the realm of a more mature vulnerability risk management program. But we all know the work of vulnerability management is never-ending. There’s still work to do. Determine the right next step for you.
To do that, ask yourself these questions:
- How big is that pile of pre-existing vulnerabilities? Keep your head down and make a dent in it.
- Does your program only focus on critical and high-severity findings? Perhaps now is the right time to incorporate medium-severity findings.
- How broad is the scope of your vulnerability management program? Are you already looking at vulnerabilities across on-prem infrastructure, cloud and applications? If not, now’s the time to start.
What’s your Vulnerability Actions Ratio?
Looking at your operational data and understanding the ratio of your vulnerability actions ratio (i.e., vulnerability findings compared to your ability to address them) will help guide you toward the best approach for improving your program.
If you’re feeling good about the state of your vulnerability ratios and need to expand the scope of your program, it might be a good time to look at additional security scanning sources.
Either way, remember that processes and having a centralized location to manage all these vulnerabilities becomes even more critical as your attack surface grows, your company scales, and you have a broader set of stakeholders to whom you must report your security and risk posture.
And since procuring new scanners in 2023 is more complicated than ever, given macroeconomic factors, now is an excellent time to assess your ratios and focus on improving processes.
_________________________
Want more practitioner perspectives? Watch our recent webinar Reframing Vulnerability Management. It features Ravi alongside fellow vulnerability management experts Martin Karel, global security and vulnerability management product lead for Nestlé, and Steve Hawkins, director of security architecture & engineering for Cambia Health.

