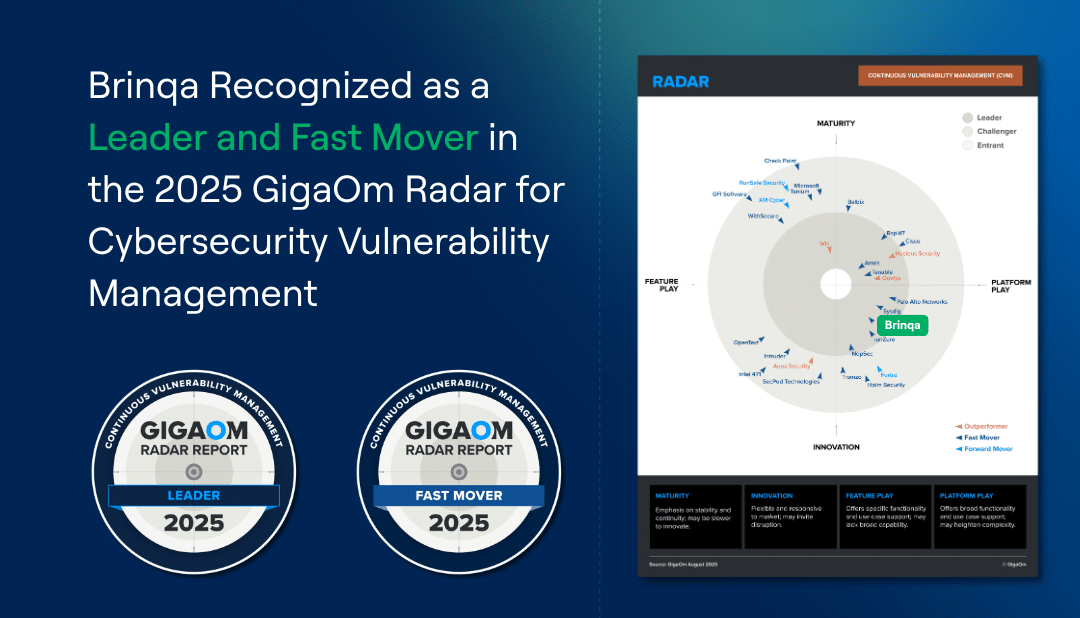
Brinqa Recognized as a Leader and Fast Mover in the 2025 GigaOm Radar for Cybersecurity Vulnerability Management
Learn MoreFeatured Resource


Brinqa Recognized as a Leader and Fast Mover in the 2025 GigaOm Radar for Cybersecurity Vulnerability Management
Learn More
How AI Is Supercharging Unified Vulnerability and Exposure Management
Learn More
Why Risk-Based Vulnerability Management Belongs at the Center of Your CTEM Strategy
Learn More
Unified Vulnerability and Exposure Management: 4 Approaches Compared
Learn More
Risk-Based Vulnerability Management Explained: How to Prioritize What Matters Most
Learn More
Brinqa and VulnCheck: Redefining Vulnerability Management
Learn More
Why Detection Obsession is Toxic for Vulnerability Management
Learn More
Wave Goodbye to the Old Way of Doing Vulnerability Management
Learn More
Stop Chasing the Adrenaline Rush of Reactive Security
Learn More