Built For an Ecosystem of Compatibility
Whether you're scanning apps, managing assets, tracking incidents, or aggregating threat intel, Brinqa brings it all together to give you a unified risk picture and automated response.
Men&Mice
Network Management

Mend
Application Security

Microsoft Azure Compute
Microsoft Azure

Microsoft Azure DevOps
IT Service Management

Microsoft Defender for Cloud
Microsoft Azure

Microsoft Defender for Cloud (GraphQL)
Microsoft Azure

Microsoft Defender for Cloud (REST)
Microsoft Azure

Microsoft Defender for Endpoint
Microsoft Azure

Microsoft Endpoint Configuration Manager
Configuration Management
Microsoft Intune
Microsoft Azure
Microsoft SCCM
Configuration Management

Microsoft Security Response Center
Threat Intelligence

Microsoft WSUS
Configuration Management

NIST NVD
Threat Intelligence
NetBox
Network Management

NetRise
Endpoint Protection

NetSPI Resolve
Application Security
Nmap
Discovery

Noname Security
Api Security

NowSecure Auto
Application Security

NowSecure Workstation
Application Security

Nozomi Networks Guardian
OT Security

OWASP ZAP
Application Security

OWASP ZAP Report
Application Security

Okta
Identity Management

Onapsis
SAP Security

OpsLevel
System Management

Orca
Cloud Security

Ordr
OT Security

PagerDuty
Incident Management
PlexTrac
Application Security

PowerShell Connector
Resource Connector
"Brinqa supports the most out-of-the-box integrations of any vendor in this evaluation."
Michael Facemire, CTO
Why Integrations Matter
Built-In Capabilities That Push Security Further
Fast, Flexible, Fully Supported
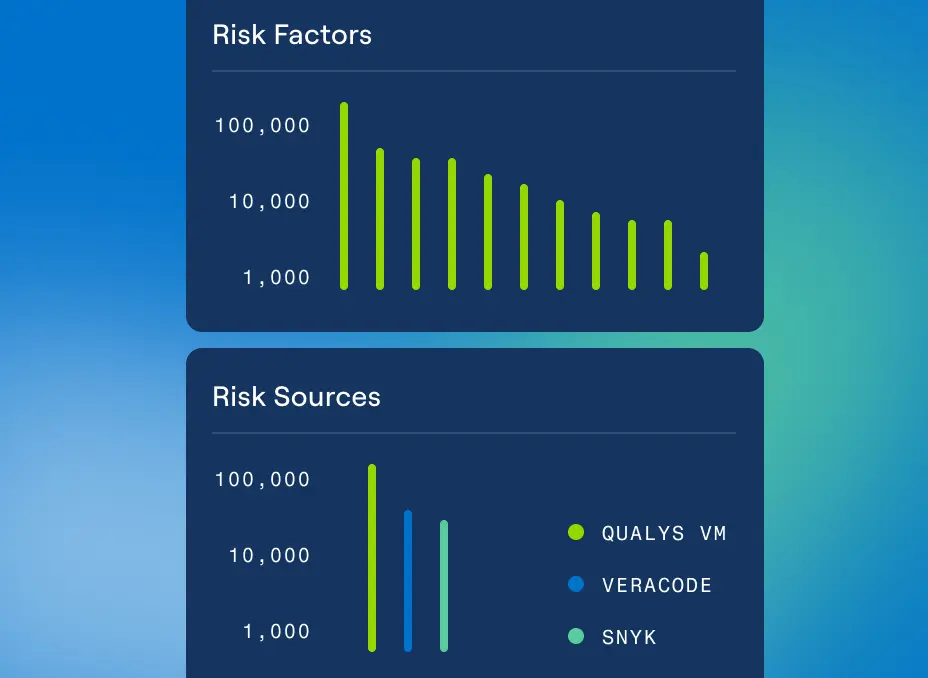
Connections That Make a Difference

Exposure Management
The CTEM Challenge: Too Many Tools, Not Enough Integration


