Built For an Ecosystem of Compatibility
Whether you're scanning apps, managing assets, tracking incidents, or aggregating threat intel, Brinqa brings it all together to give you a unified risk picture and automated response.

Snyk
Application Security

SonarQube
Application Security

Sonatype Nexus IQ
Application Security

Splunk
Security Analytics

StackRox
Container Security

Synack
Application Security

Tanium Asset
Asset Management

Tanium Comply
Vulnerability Management

TeamDynamix
IT Service Management

Tenable Nessus
Vulnerability Management

Tenable Security Center
Vulnerability Management

Tenable Vulnerability Management
Vulnerability Management

Tenable Web App Scanning
Application Security

Tenable.io
Vulnerability Management

Tenable.io Web App Scanning
Application Security

Tenable.sc
Vulnerability Management

ThreatConnect
Threat Intelligence

Trend Micro Cloud Conformity
Cloud Security

Trend Micro Deep Security
Endpoint Protection

Tripwire Enterprise
Compliance Management

Tripwire IP360
Vulnerability Management

TruSTAR
Threat Intelligence

Uptycs
Security Analytics

Veracode
Application Security

VulnDB
Vulnerability Management
WhiteHat Sentinel
Application Security

Windows Cmd Connector
Resource Connector

Wiz
Cloud Security

Xml Connector
File

Zoom
Unified Communications

endoflife.date
Application Security

runZero
Asset Management
"Brinqa supports the most out-of-the-box integrations of any vendor in this evaluation."
Michael Facemire, CTO
Why Integrations Matter
Built-In Capabilities That Push Security Further
Fast, Flexible, Fully Supported
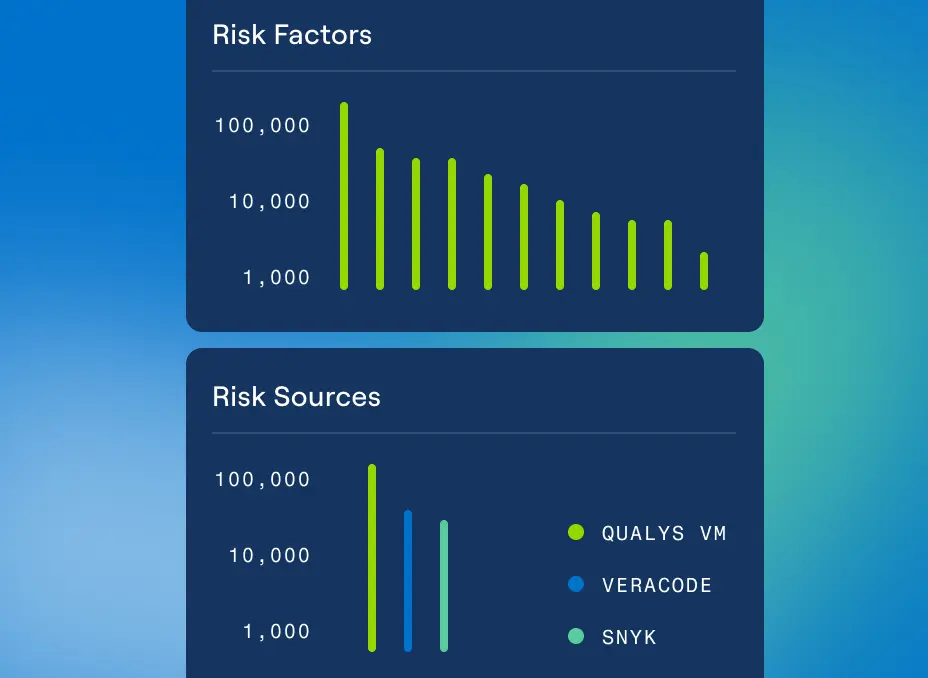
Connections That Make a Difference

Exposure Management
The CTEM Challenge: Too Many Tools, Not Enough Integration


