
How to Prioritize Vulnerabilities: A Modern Guide to Risk-Based Remediation
Read Blog
How to Prioritize Vulnerabilities: A Modern Guide to Risk-Based Remediation
Learn More


Case Study: PhonePe’s Build vs. Buy Decision to Level Up Application Security Posture Management
Learn More
CISO Perspective: The Real Open Source Risk Isn’t the Code
Learn More

EPSS vs. CVSS: Understanding the Differences and Use Cases
Learn More
Automated Vulnerability Remediation Explained: Best Practices for Reducing Real-World Risk
Learn More
Risk-Based Vulnerability Management Explained: How to Prioritize What Matters Most
Learn More
Gartner® Report: How to Grow Vulnerability Management Into Exposure Management – Brought to You by Brinqa
Learn More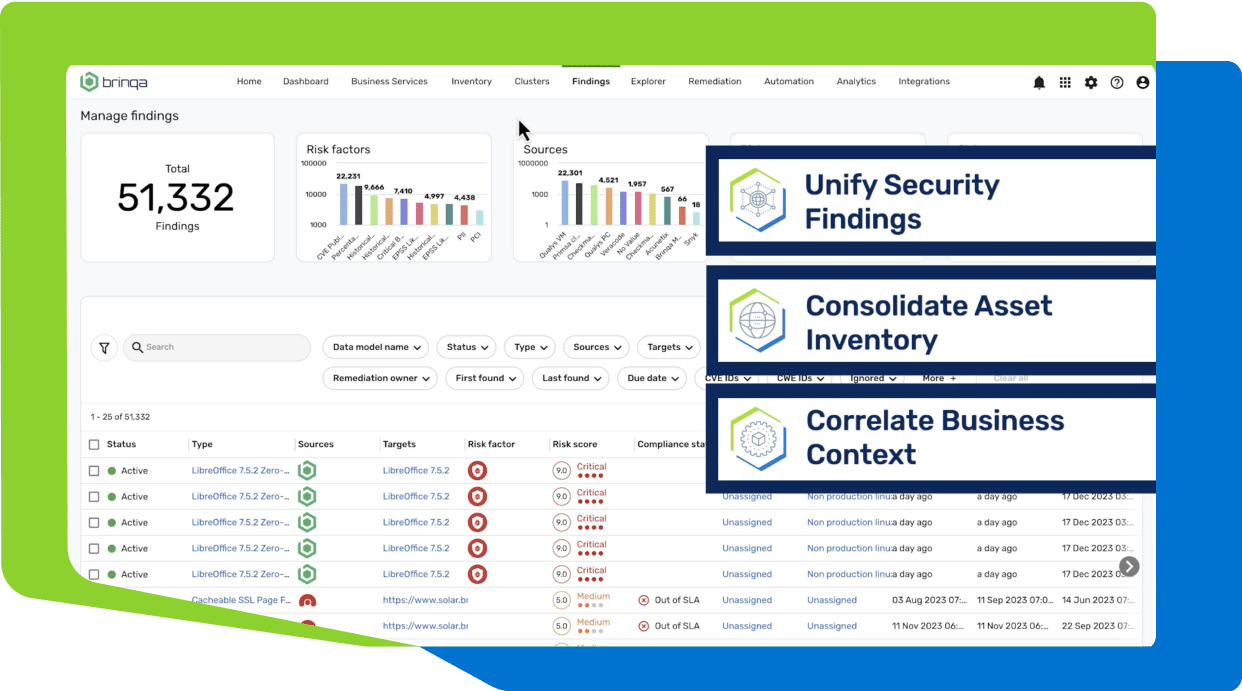
What Does the Skybox Shutdown Mean for Vulnerability Management—And What Comes Next?
Learn More
Microsoft and Wiz Moves Signal Threat Exposure Management Momentum
Learn More