Risk Operations Center – The New Approach for Proactive Cybersecurity
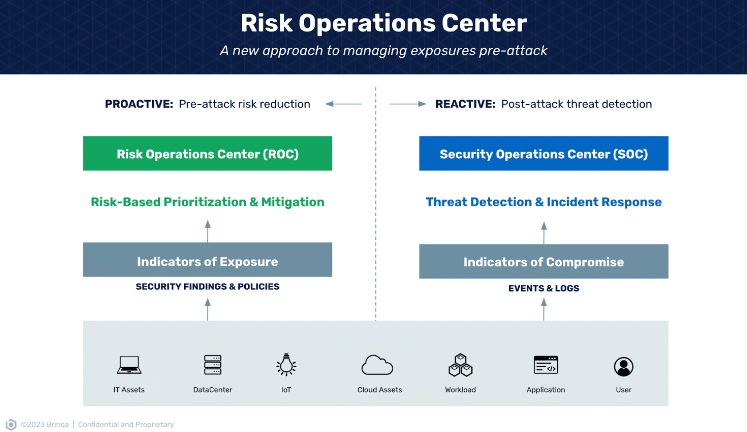
It is time for the Vulnerability Management discipline to evolve into a Risk Operations Center (ROC). A proactive security approach that combines operational rigor, risk-based management of vulnerabilities and security policies across the entire attack surface, and business level communications about risk. It also serves to elevate proactive security to be on par with detection and response strategies represented by the SOC.
The focus is no longer on chasing every vulnerability, nor is it about managing high-impact vulnerabilities in a state of perpetual crisis. Instead, the ROC champions a more calculated approach. By offering a holistic view across the entire business while maintaining the precision to zero in on the most pressing threats and remediate them before they can be weaponized. This is not just a technological shift in focus, it is a cultural one as well.
The other key aspect of a Risk Operations Center is bridging the gap with business units by reorienting the dialogue away from a purely technical vocabulary filled with infrastructure details and CVEs to a business-centric risk narrative.
This approach fosters a heightened understanding of risk. It promotes accountability on business units and risk owners, firmly placing kudos and responsibility where they belong. Security is no longer responsible for just finding risks, but leading a collective organizational endeavor to understand potential impact and address the threats that the company’s risk-tolerance mandates.
At the heart of the ROC’s ethos is operational excellence. This means appling a concerted effort to operationalize the cyber risk lifecycle across an organization’s entire attack surface. Additionally, the ROC does not only consider vulnerabilities and findings reported by security tools, but also considers violations of security policies on the same level as a vulnerability exposure.
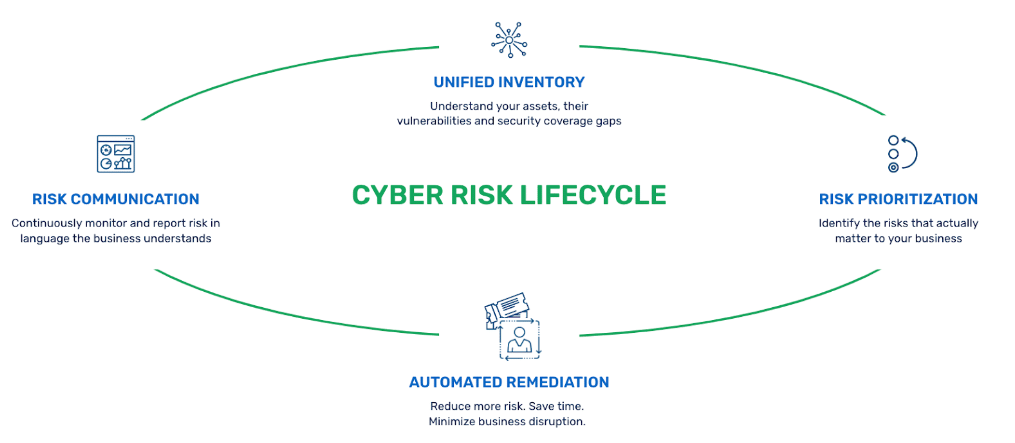
Central to its efficacy is how the ROC leverages the cyber risk lifecycle. It starts by creating a Unified Inventory of all assets and the vulnerabilities associated with them. Further business context is added, to capture the relationships between assets that make up business critical applications, and asset ownership.
This inventory is what contains the critical information for the next phase of the cyber risk lifecycle, Risk Prioritization. Risk scores are automatically produced based on the CVEs themselves, business context to understand the role in the business and threat intelligence to further refine the likelihood of exploit within the organization. The result is a precise list of vulnerabilities — from across all security disciplines — that put the business at risk, a crystal clear understanding of who is responsible to fix them, and what needs to be done to fix them.
Armed with a trusted list of vulnerabilities that need to be addressed, Automated Remediation manages the remediation ticketing process. From sending the remediation tickets to the right technical owner in their own ITSM workflow tool, to validating fixes once a ticket is closed, all parts of the remediation process are tracked. Security teams have the visibility to track SLAs, understand which teams are addressing their vulnerabilities, and which are not.
The final stage of the lifecycle is Risk Communication, where the security team translates the cyber security posture of the organization into language and terms the rest of the business can understand. Once again this is where the business context and ownership information contained in the unified inventory is put to work.
A Shift in Culture
Adopting a proactive approach to security via a Risk Operation Center is not just a question of technology, it also requires a shift in culture. It requires that the CISO and senior security leaders are ready to hold business owners accountable. It requires the security leadership to understand the priorities of the business, to accept risks they potentially wouldn’t in a purist mindset, and to be the translators from technical security speak into business relevant risk.
Business owners must trust that security is only going to ask them to address issues that are truly important. They must also agree to hold their own people accountable to fix such issues with the priority they deserve.
At the end of the day, a security culture of trust, speed, and efficacy are the ultimate values a Risk Operations Center delivers.
Benefits of Implementing a Risk Operations Center
A ROC comes with numerous benefits to mature organizational security posture:
- Proactive Risk Management – ROCs proactively anticipate and pinpoint potential risks, allowing organizations to implement preventative measures. This ensures timely and precise mitigation of vulnerabilities, crucial for reducing their potential impact.
- Centralized Oversight – ROC centralizes cyber risk management, preventing data silos and promoting cohesive decision-making. Findings from various tools are consolidated, with remediation requests directed to teams via platforms they already use, like Jira. Upon resolution, feedback loops with the originating tools track SLAs, allow rescanning, and ensure vulnerabilities are effectively addressed.
- Cost Savings – By proactively managing risks and reducing the potential impact of threats, organizations can avoid costly incidents and data breaches, leading to significant long-term cost savings. Security teams can also identify redundant security tooling and reduce unneeded security spend.
- Enhanced Collaboration and Communication – Centralizing risk operations enhances inter-team communication and collaboration, fostering coordinated threat responses. With security taking on the role of translating, organizations save time and money by more rapidly addressing risks.
- Improved Compliance and Reporting – A ROC not only aids in ensuring compliance with industry-specific risk management and data protection standards but also creates a comprehensive record of risk and vulnerability management, demonstrating a mature lifecycle of tracking, remediation, and SLA reporting.
- Scalability and Adaptability – As the cyber risk environment changes, ROCs scale and incorporate new tools, aligning with a customer’s existing technology stack rather than forcing the tech to fit the ROC.
Learn why Asurion considers Brinqa at “the heart of their risk operations center”, in this on-demand recording.
If you would like to learn more about the Brinqa Platform, sign up for a demo.


