Built For an Ecosystem of Compatibility
Whether you're scanning apps, managing assets, tracking incidents, or aggregating threat intel, Brinqa brings it all together to give you a unified risk picture and automated response.

BloodHound Enterprise
Identity Management

Brinqa Connect
Data Store

Brinqa Risk Intelligence
Threat Intelligence

Bugcrowd
Application Security

Burp Suite
Application Security

Burp Suite Enterprise
Application Security

Burp Suite Pro
Application Security

CA Service Desk Manager
IT Service Management

CISA Known Exploited Vulnerabilities
Threat Intelligence

CSV Connector
File
Carbon Black Platform
Endpoint Protection
Cb Response
Endpoint Protection
Censys
External Attack Surface Management

Check Point CloudGuard
Cloud Security

Checkmarx
Application Security

Checkmarx CxSAST Connector
Application Security

Checkmarx One
Application Security

Checkmarx SAST
Application Security

Checkmarx SCA
Application Security

Cherwell
IT Service Management

Cisco
Network Management
Claroty
OT Security

Claroty xDome
OT Security

CloudBolt
Cloud Management

CloudKnox
Identity Management

Cobalt
Application Security

Contrast Security
Application Security

Cortex
System Management

Cortex Xpanse
External Attack Surface Management

Coverity
Application Security

CrowdStrike
Endpoint Protection

CrowdStrike Cloud Security
Cloud Security
"Brinqa supports the most out-of-the-box integrations of any vendor in this evaluation."
Michael Facemire, CTO
Why Integrations Matter
Built-In Capabilities That Push Security Further
Fast, Flexible, Fully Supported
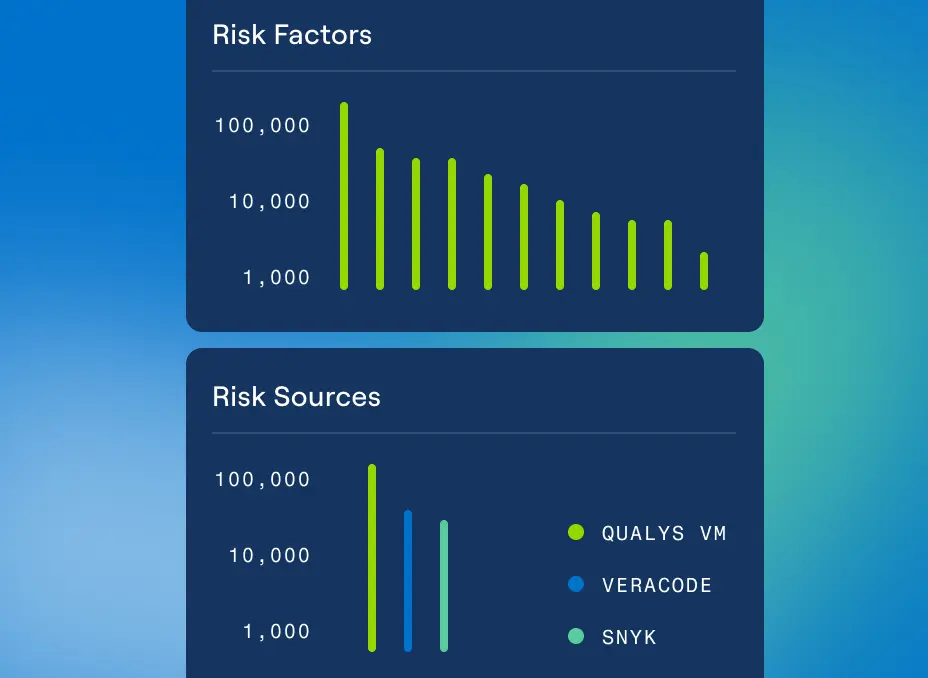
Connections That Make a Difference

Exposure Management
The CTEM Challenge: Too Many Tools, Not Enough Integration


