Nov 22, 2024
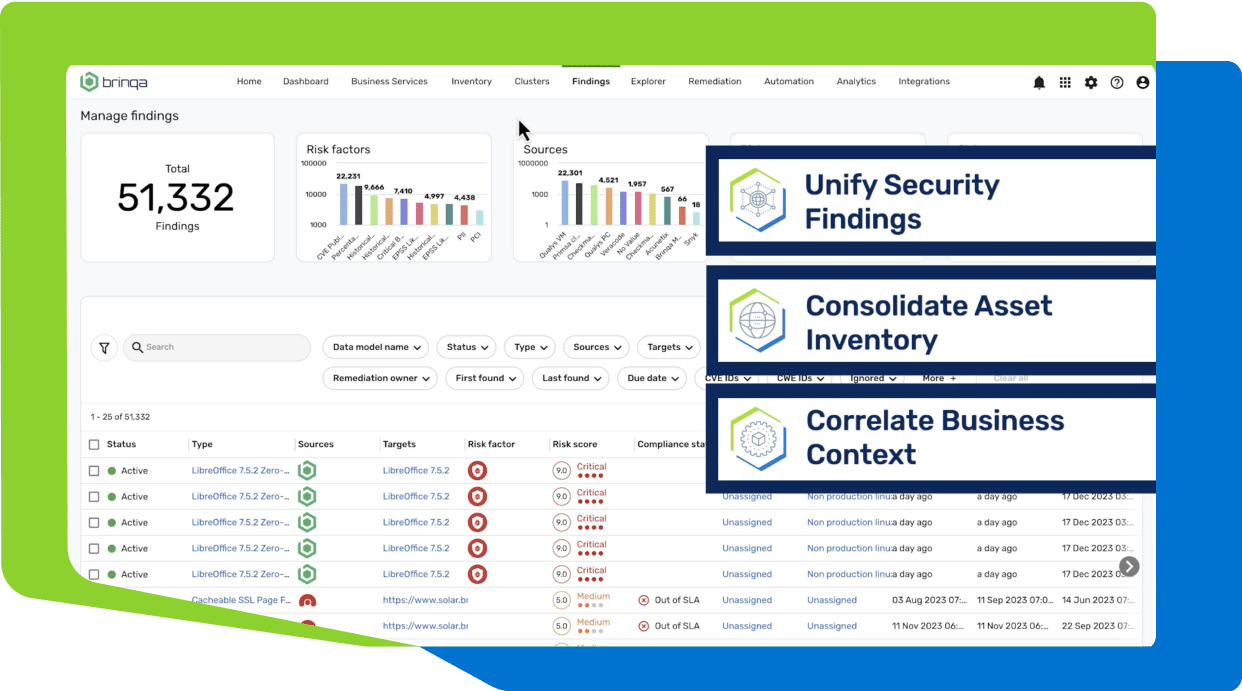
Microsoft and Wiz Moves Signal Threat Exposure Management Momentum



Are You Struggling with One of These Top Vulnerability Management Challenges?
Learn More
Risk Operations Center – The New Approach for Proactive Cybersecurity
Learn More