
Vulnerability Management Integrations Checklist
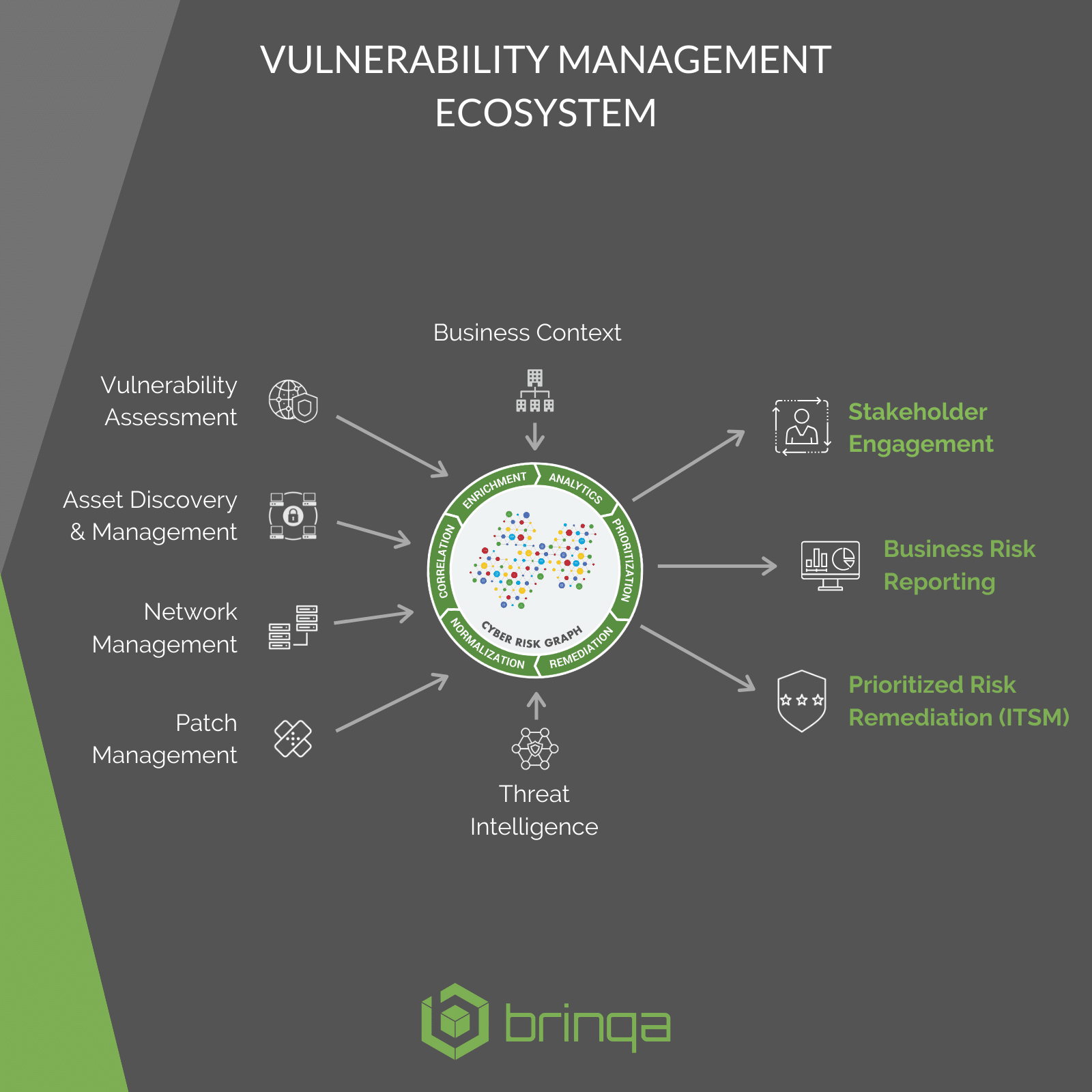
Risk-based Vulnerability Management requires precise coordination of data and workflows across several classes of security products. This document highlights important integrations to consider when designing your VM program and lists available Brinqa connectors.
Highlights
- Vulnerability Assessment — primary source of vulnerability enumeration, and often device discovery.
- Asset Discovery & Management — source of invaluable business context crucial for effective risk prioritization and remediation.
- Threat Intelligence — factors of exploitability and indicators of compromise that can mean the difference between a breach and a secured environment.
- Network Management — can help organizations understand the true structure of their networks to be leveraged for attack path analysis.
- Patch Management — can drastically improve remediation efficiency and help achieve true closed-loop remediation.
- IT Service Management — bi-directional integrations to govern automated ticket creation and management.