How to Automate Vulnerability Prioritization

As the number of known (and exploited) vulnerabilities steadily grows, a consistent and sustainable vulnerability prioritization process remains key to efficiently managing competing risks and protecting IT systems and data. An automated approach helps security teams methodically rank vulnerabilities based on risk factors that include security context, threat intelligence and business impact.
But how do you prioritize critical vulnerabilities? Automation is the solution, streamlining the manual process of ranking vulnerabilities, reducing your attack surface, and refocusing your resources on autopilot.
Let’s review a few key points for how to automate vulnerability prioritization, breaking down the process step-by-step.
What Is Automated Vulnerability Prioritization and Why Do You Need It?
Automated vulnerability prioritization ranks risks in your environment using data from various vulnerability data sources and critical business context. It considers factors such as severity, exploitability, asset value, and threat intelligence.
Ponemon Institute research shows that attackers cannot realistically exploit 85% of your organization’s vulnerabilities. The challenge is knowing which vulnerabilities can safely be deprioritized while identifying the 15% that pose real risk based on severity, exploitability, and potential impact on your business.
As the number of vulnerabilities grows, the workload to assess and remediate is already overwhelming vulnerability management teams, so it’s important to streamline and automate scanning, validation and prioritization using both threat and business context to quickly sort through the noise and focus on what matters. Filtering out non-exploitable security risks without the need for manual ranking increases the efficiency across DevSecOps, AppSec, and IT operations by reducing time spent on non-issues, allowing teams to reduce risk.
The Cybersecurity and Infrastructure Security Agency (CISA) insights warn that cyber attackers can exploit a vulnerability within 15 days of discovering it. This statistic is troubling, especially considering that the mean time to remediate a critical vulnerability in a web application, for example, is 35 days, according to Edgescan. Organizations like Nestle have eliminated the window for exploitation by consolidating and prioritizing critical threats through automation and unified vulnerability management, improving their overall security posture.
Benefits of Implementing an Automation Solution
Vulnerability prioritization automation offers numerous benefits in comparison to manual efforts:
| Areas of improvement | How vulnerability prioritization improves with automation |
|---|---|
| Efficiency and accuracy | Minimizes the risk of potential bias and human error by consistently assessing vulnerabilities in real time. |
| Scalability | Adapts dynamically to an expanding attack surface, effectively managing a growing number of vulnerabilities as the number of users, devices, and software increases. |
| Risk management | Streamlines security efforts by focusing on critical vulnerabilities, allowing teams to allocate their time and technology where the impact is greatest and effectively reduce threat exposure. |
| Cost-effectiveness | Reduces manual efforts required in vulnerability risk management, lowering operational costs by automating repetitive and time-consuming tasks. |
Learn the basics of risk-based prioritization with our guide.
Steps to Automate Vulnerability Prioritization
Follow these five steps to implement an effective automated vulnerability prioritization framework:
1. Integrate and Enrich Data
Here’s how to properly consolidate your vulnerabilities, exposures and other data sources before feeding into your automated workflow:
- Consolidate vulnerability data: Combine and normalize data from Dynamic Application Security Testing (DAST), Static Application Security Testing (SAST), network scanners, and cloud security tools. This is essential before considering prioritization frameworks like EPSS because you must account for all elements of an organization’s infrastructure, including cloud, on-premises and application assets to assess potentially business-disrupting vulnerabilities associated with them.
- Map vulnerabilities to affected assets: Integrate your asset inventory and configuration management databases to consolidate IT asset records and correlate them with critical vulnerabilities tied to them.
- Enrich your data with asset context: Add asset information, such as software versions and data sensitivity, and layers of contextual information, like previous security incidents.
- Integrate threat intelligence feeds: Connect intelligence feeds to stay updated on vulnerabilities actively exploited in the wild.
With over 200 integrations, many of which include pre-built attribute mappings, Brinqa simplifies the process of consolidating and normalizing data from tools across your IT and security ecosystem.
Watch this on-demand webinar to explore how business context can help reframe your risk prioritization.
2. Visualize Your Risk
With all your data sources integrated, including threat intelligence, added business context, and tribal knowledge, you can now get a comprehensive view of the risks to your environment.
Brinqa’s Cyber Risk Graph allows you to create a live model of your attack surface. A complete model will help you better understand the relationships between your assets, threat intelligence, and vulnerability data within the specific context of your business. With robust visibility, you can:
- See all of the vulnerabilities and exposures that exist across your business at a glance.
- Cluster your related risks to get tailored perspectives of your attack surface.
- Simplify the process of identifying who owns at-risk assets.
3. Prioritize Vulnerabilities Based on your Definition of Risk
Using a Smart Scoring system that understands your unique attack surface, you can rank vulnerabilities based on risks that matter to your business. That means, going beyond a Common Vulnerability Scoring System (CVSS) that doesn’t give a complete picture of your exposure.
Smart scoring considers additional factors such as:
- Vulnerability exploitability
- Asset business criticality
- Potential operational impacts
- Threat intelligence
The scores are normalized, taking into account the correlations between applications, infrastructure, priorities, and exploits. With Brinqa, you can further customize your scores to account for specific risk factors relevant to your business, ensuring that even less critical threats are evaluated based on their potential impact on your unique environment.
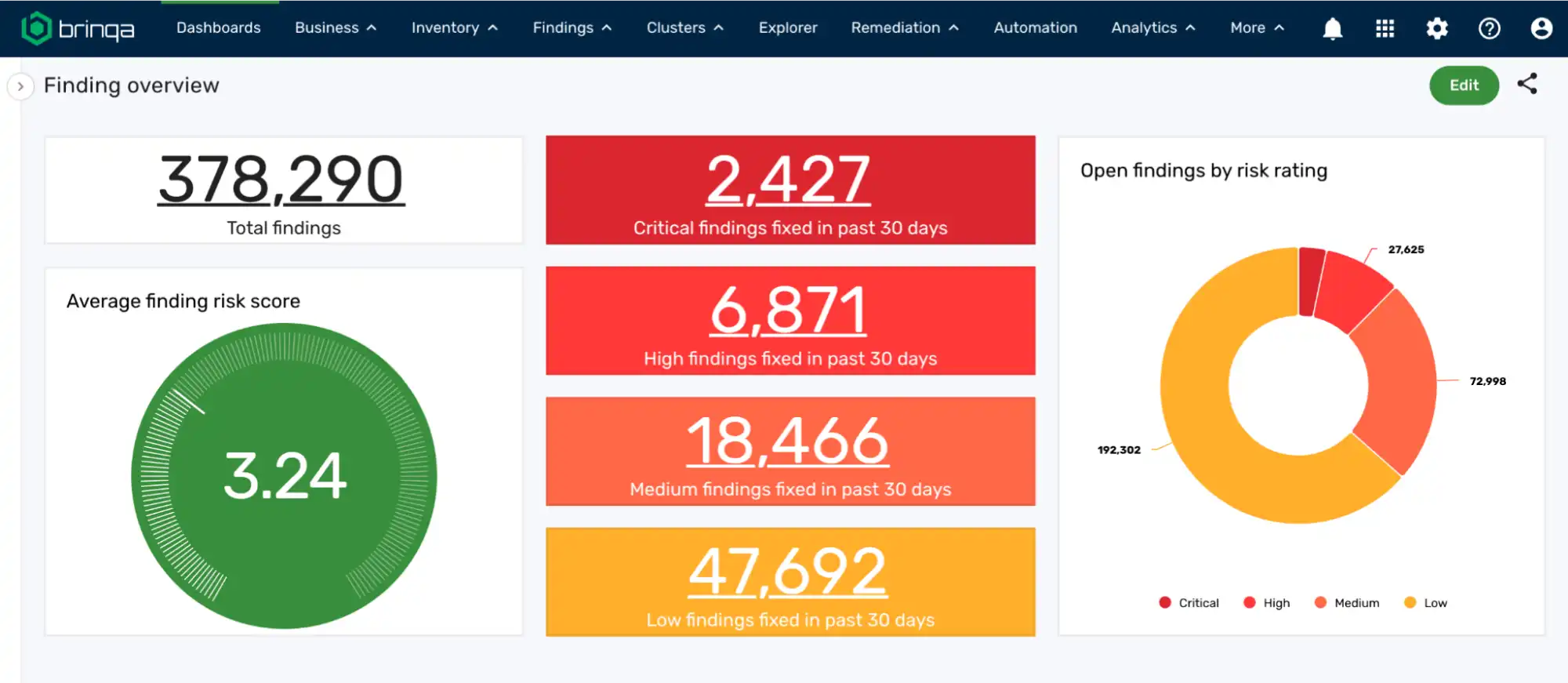
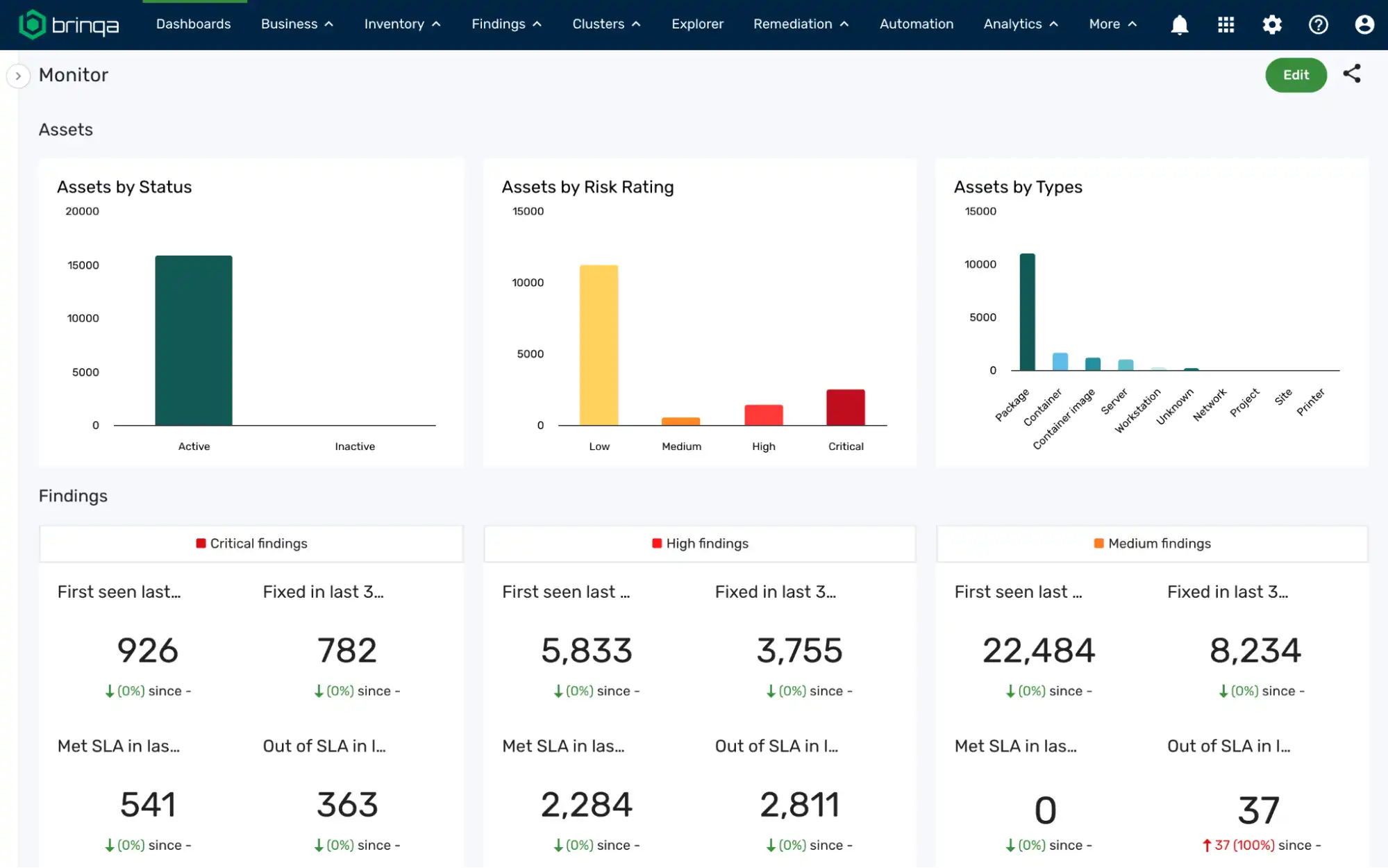
Brinqa’s vulnerability management platform also provides dashboards and reports to present these prioritized vulnerabilities and their specific risk factors, ensuring your business and remediation teams can understand and properly act on security threats.
4. Integrate with Remediation Workflows
Automated vulnerability remediation with precise response ensures that identified vulnerabilities are prioritized and addressed. A focused approach to combining your prioritization and remediation process includes:
- Instant ticket creation: Automate your tickets, grouping them intelligently to help reduce the volume and pushing them to the right owners in real time.
- Clear remediation instructions: Include specific remediation guidelines for each ticket to ensure appropriate actions for the particular vulnerability and asset configuration.
- Integrated two-way sync: Keep your vulnerability management system and IT service management (ITSM) tools in sync to easily share real-time updates on remediation progress.
- Automated remediation actions: Speed up routine tasks such as applying patches or updating configurations using automated vulnerability remediation tools.
- Defined exceptions: Create workflows to efficiently handle situations like acceptable risks or false positives, freeing up your security team for critical issues.
- Validated remediation: Ensure your automation confirms that remediation actions have effectively mitigated the vulnerabilities.
5. Continuously Assess Vulnerability Data
By constantly pulling new vulnerability intel from multiple tools and data sources, you can maintain up-to-date security, ensure a robust defense mechanism, and quickly identify and mitigate potential threats.
This proactive approach to cybersecurity, central to a Risk Operations Center (ROC), equips your organization to proactively minimize the risk of security breaches effectively and enhances risk-based management of vulnerabilities across the entire attack surface.
Learn how Nestle built a unified vulnerability management framework on Brinqa.
Brinqa Makes Vulnerability Prioritization Automation a Seamless Process
With The Brinqa Platform, you can streamline enterprise vulnerability management prioritization and automate every stage of the cyber risk lifecycle. Combine security findings, asset information, and business context to create a detailed model of your organization’s attack surface. Brinqa calculates risk ratings based on business priorities and the connections between threats and assets.
Brinqa’s automation enhances remediation, from intelligent ticket routing and notifications to thorough closed-loop verification. Customizable risk reporting dashboards provide stakeholders with clear, actionable insights, enabling organizations to prioritize remediation efforts and reduce critical vulnerabilities by up to 75%.
Experience the power of Brinqa’s platform. Book a demo with one of our experts.